Data at Rest Encryption
Satisfy security and regulatory requirements such as PCI-DSS and HIPAA while protecting your data from loss via theft, security breach, during repair, or as part of disposal.
Encryption is Non-negotiable
Capabilities & Benefits
AES-256 Software Encryption
Nutanix native software-based encryption is a simple to deploy and cost-effective option designed for Nutanix HCI. Leveraging a NIST certified FIPS 140-2 level 1 compliant encryption module, AOS software encryption is ideal for most use cases.
Built-In Key Management
Nutanix provides native data security without any mandate for a third party key manager. Securely store keys and eliminate the need to procure a third-party solution.
Hardware-Based Encryption
Nutanix fully supports the use of Self-Encrypting Drives (SED). Though more costly, they are ideal for use cases where a hardware-based solution is required for regulatory or policy compliance. Additionally, Nutanix supports dual encryption by layering software over hardware-based schemes.
Enterprise Key Management
Nutanix software and hardware encryption can utilize existing Enterprise Key Management (EKM) solutions. Easily migrate between Nutanix native and EKM.
The Nutanix Approach to Encryption
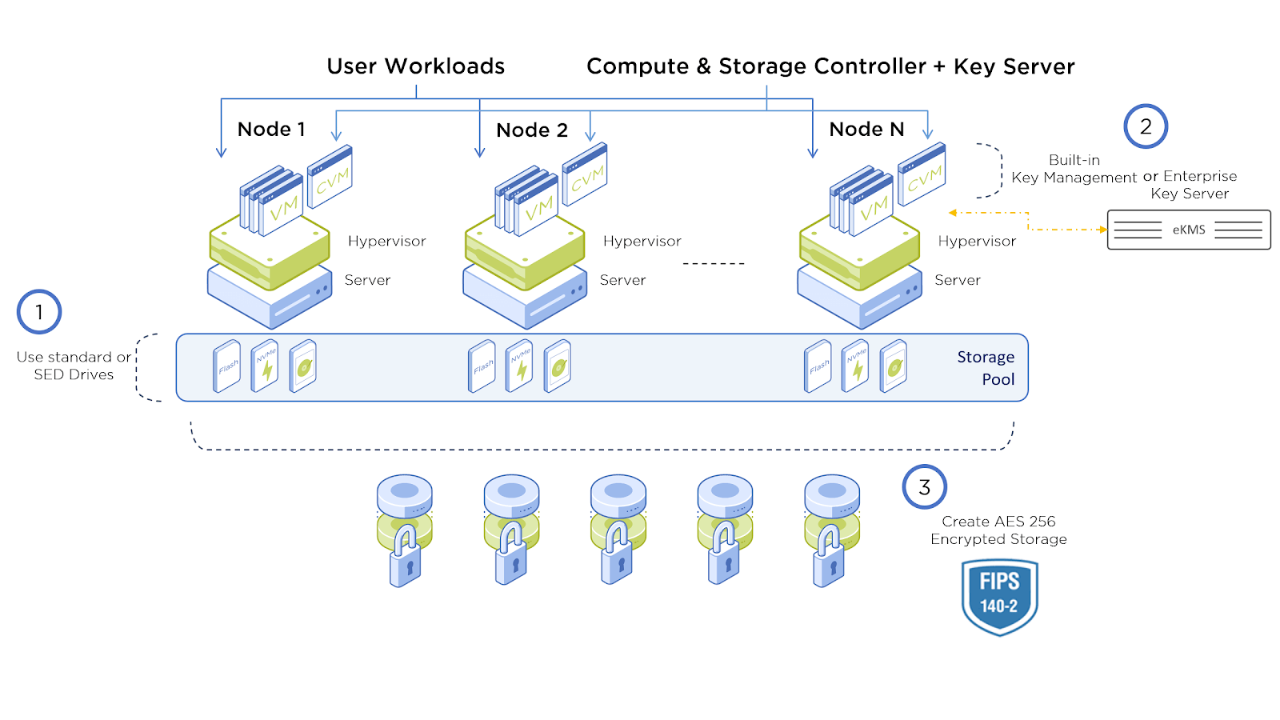
With Nutanix AOS, Data-at-Rest Encryption can be done entirely in software. Though also supported, there's no need for self-encrypting drives (SEDs) or an external key management solution (KMS).
With nothing additional to install or manage, you can add FIPS compliant data-at-rest encryption to your HCI environment in minutes.
Learn More
Related Products & Services

Hyperconverged Test Drive
Try the Industry-Leading Hyperconverged Infrastructure Today!




