Cyber Attacks are on the Rise
Complexity Causes Vulnerability
Modern data centers are complex. Complexity is the enemy of information security. Increased attention on the public and hybrid cloud will only increase that complexity.
Threats Are Growing Rapidly
Your data is valuable. Cyber attacks are growing in frequency and sophistication. Research shows a 350% growth in ransomware attacks alone.
Data Breaches Are Costly
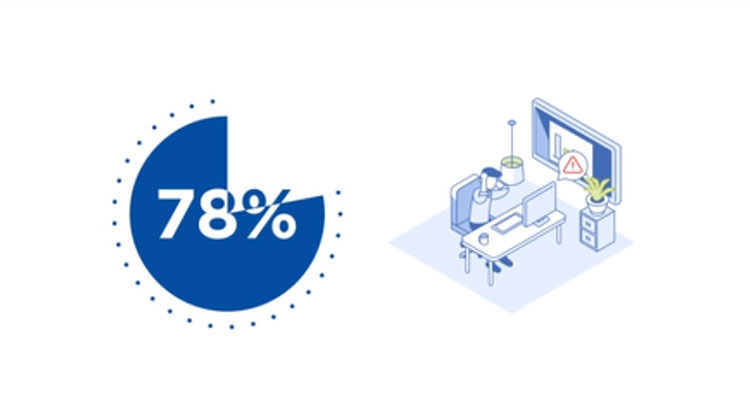
78% of organizations have been victims of one or more successful cyberattacks, with each data breach costing an average of $3.86M.
Enterprises are Embracing "Zero Trust"
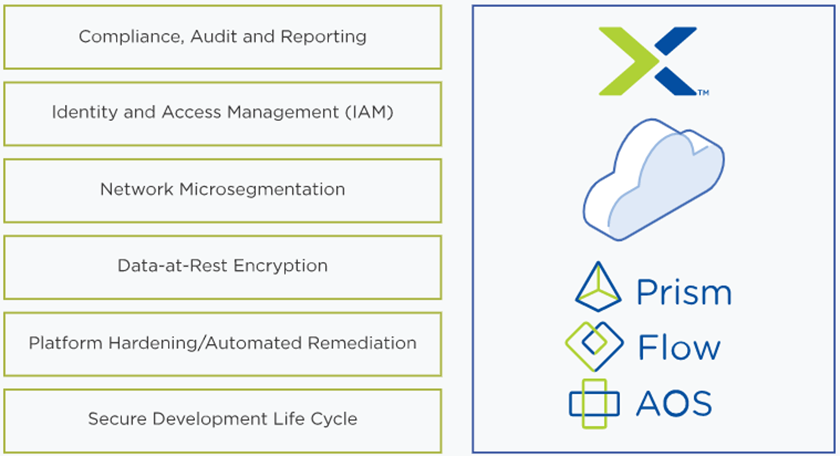
Zero Trust is a security design philosophy that assumes that any network, application, server, or user could be compromised versus designating trusted and untrusted categories of assets thus we must design our security protocols around that assumption.
Learn More
What the Experts Are Saying
Resources

A Defense in Depth Strategy
Security in the enterprise datacenter begins with a robust infrastructure foundation. Read the solution brief to learn how Nutanix help address key security concerns

Take a Security-First Approach
To better fortify your front line of defense against security attacks, it’s important to look at your infrastructure and see if it utilizes a security-first approach. Simple and effective, security-first infrastructure tackles the pains associated with security management
Data-at-Rest Encryption Simplified
As cyber attackers become more sophisticated, business simply can't afford to have any vulnerable gaps. But too many overlook the all-important task of data encryption, which is critical to providing another countermeasure against breaches.

Securing Citrix Virtual Apps and Desktops
Protecting VDI desktops and infrastructure VMs for your critical Citrix Virtual Apps and Desktops deployment on AHV is easy, secure, and scalable.

Security at the Virtualization Layer
One of the benefits of virtualization is security; applications running in separate virtual machines are isolated from each other and, ideally, it is very hard for a compromised guest to attack other virtual machines running on the same host.

Preventing Ransomware
There is no single action, software solution, or security control that can completely safeguard your organization from ransomware. In this Nutanix Tech Brief, we outline Nutanix capabilities, industry best practices, and techniques to incorporate into your cybersecurity defense strategies when using Nutanix.