UPDATE - Since the release of this blog our encryption solution has evolved with many new features and functions. Please visit our data-at-rest encryption solution page for current details.
In a previous article I published the first part of a multi-month announcement for NOS 4.1 (Nutanix 4.1 Features Overview (Beyond Marketing) – Part 1). As part of the announcement I disclosed the new Data-at-rest encryption feature.

Nutanix clusters are deployed in a variety of customer environments requiring different levels of security, including sensitive/classified environments. These customers typically harden IT products deployed in their datacenters based on very specific guidelines, and are mandated to procure products that have obtained industry standard certifications.
Data-at-rest encryption is one such key criteria that customers use to evaluate a product when procuring IT solutions to meet their project requirements. Nutanix data-at-Rest encryption satisfies regulatory requirements for government agencies, banking, financial, healthcare and other G2000 enterprise customers who consider data security products and solutions.
The data-at-rest encryption feature is being released with NOS 4.1 and allow Nutanix customers to encrypt storage using strong encryption algorithm and only allows access to this data (decrypt) when presented with the correct credentials, and is compliant with regulatory requirements for data at rest encryption.
FIPS 140-2 Level-2 Compliant
Nutanix data-at-rest encryption leverages FIPS 140-2 Level-2 validated self-encrypting drives, making it future proof since it uses open standard protocols KMIP and TCG.
“The National Institute of Standards and Technology (NIST) issued the FIPS 140 Publication Series to coordinate the requirements and standards for cryptography modules that include both hardware and software components…. The standard provides four increasing, qualitative levels of security intended to cover a wide range of potential applications and environments. The security requirements cover areas related to the secure design and implementation of a cryptographic module.” – Wikipedia
FIPS 140-2 defines four levels of security, simply named “Level 1″ to “Level 4″. It does not specify in detail what level of security is required by any particular application.
Security Level 1
Security Level 1 provides the lowest level of security. Basic security requirements are specified for a cryptographic module (e.g., at least one Approved algorithm or Approved security function shall be used). No specific physical security mechanisms are required in a Security Level 1 cryptographic module beyond the basic requirement for production-grade components.
Security Level 2
Security Level 2 improves upon the physical security mechanisms of a Security Level 1 cryptographic module by requiring features that show evidence of tampering, including tamper-evident coatings or seals that must be broken to obtain physical access to the plaintext cryptographic keys and critical security parameters (CSPs) within the module, or pick-resistant locks on covers or doors to protect against unauthorized physical access.
As an example, FIPS 140-2 is a requirement to achieve compliance with the HIPAA standard to protect healthcare data. Already mandated by the U.S. Department of Defense (DoD) for encryption, FIPS 140-2 is a powerful security solution that reduces risk without increasing costs.
Supported Encryption Features
The first supported encryption features within Nutanix are:
- Instantaneous enable/disable encryption
- Encrypt data at rest at a cluster-wide level
- Instantaneous Secure Erase disk(s)
- Rotate passwords per security policy
- Ability to enable/disable on-disk encryption with live data
- Ability to transform the cluster from a secure configuration to non-secure configuration (and vice-versa)
- Secure-Erase (using Crypto Erase) the specific partition and subsequently use it for storing data from other partitions that are being marked un-secure
- Instantaneous Secure Erase disk(s) using Crypto Erase
How does Nutanix Data-at-rest encryption work?
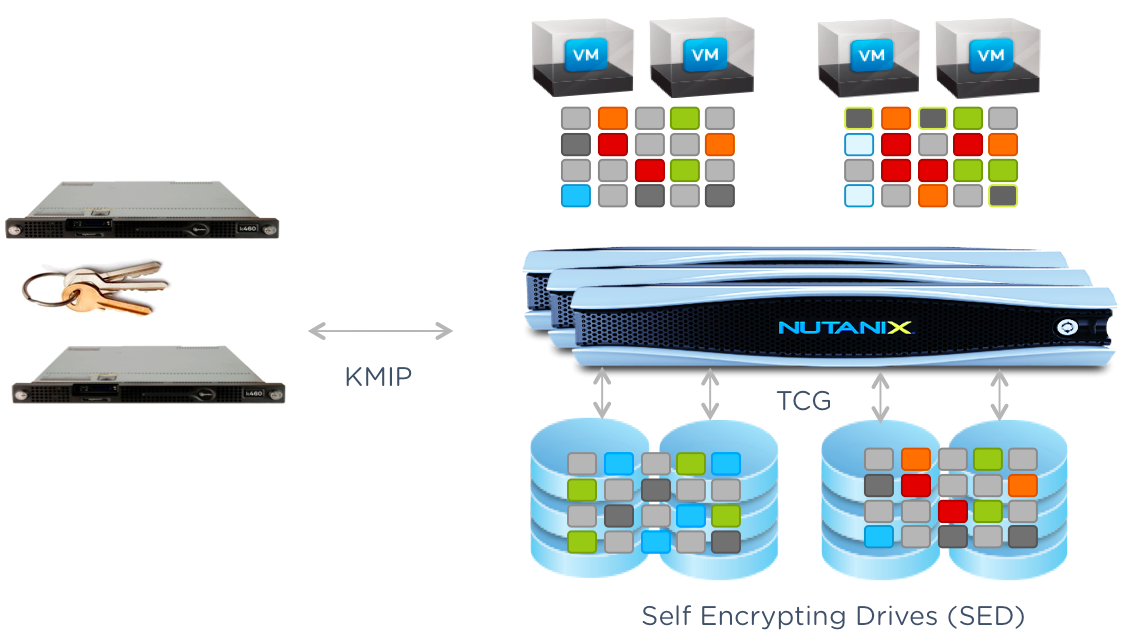
To enable Nutanix Data-at-rest encryption a 3rd party Key Management server is required. At the time of the launch only ESXi is supported and only the SafeNet KeySecure Cryptographic Key Management System is certified, but other key management systems will be supported.
Nutanix supports any KMIP 1.0 compliant key management system, but others have not yet been certified. The key management system can even be a VM running on another Nutanix cluster, and since Nutanix leverage hardware encryption using the self-encrypting drives the performance impact on the cluster is minimal.

Nutanix clusters do not come with data-at-rest encryption turned on by default and it has to be turned on by the administrator using the PRISM UI or nCLI. The PRISM UI provides a simple and easy way to management Key Management Device details and Certificate Authorities.
Each Nutanix node automatically generates an authentication certificate and adds it to the Key Management Device. At this point the nodes also auto-generate and set PINs on their respective FIPS validated SED drives. The Nutanix controller in each node then adds the PINs to the Key Management Device.
Please note that once the PIN is set on an SED, you need the PIN to unlock the device (lose the PIN, lose data). The PIN can be reset using the SecureErase primitive to ‘unsecure’ the disk/partition, but all existing data is lost in this case. This is important to understand, in case you are moving the drives between clusters or nodes.
The ESXi and NTNX boot partition remain unencrypted – SEDs support encrypting individual disk partitions selectively using the ‘BAND’ feature (a range of blocks).
Data-at-rest Deployment Considerations
In this first release it is not possible to mix a Nutanix data-at-rest encryption enabled cluster with a non-encryopted cluster because the platform requires special FIPS 140-2 Level 2 SED drives to meet the data at rest encryption requirements. By breaking the homogeneity of the cluster, one will violate the data at rest encryption requirement for copies of data stored on non-SED drives. However, both encrypted and non-encrypted clusters can be managed via single-pane of management using PRISM Central.
Data in-flight is NOT encrypted, that means data being transmitted between virtual machines and the Nutanix CVM are not encrypted. Data is only encrypted once they touch the SED drives, either SSD or HDDs. In saying that, the Nutanix Controller VM has been exceptionally hardened and is being put trough a number of security checks, validations and certifications.
The Nutanix Cloud Connect, also introduced in my article Nutanix 4.1 Features Overview (Beyond Marketing) – Part 1 will also support at-rest encryption using Server Side Encryption.
This article was first published by Andre Leibovici (@andreleibovici) at myvirtualcloud.net.