Networking that is Powering Hybrid Multicloud Mobility
By Dwayne Lessner
Principal Technical Marketing Engineer
Nutanix
In a recent blog, I discussed how the storage options in the Nutanix Cloud Clusters (NC2) platform are allowing businesses to regain the flexibility they need. Now I want to take a look at how Nutanix is doing the same thing for networking with the Nutanix Flow Virtual Networking (FVN) solution with mobility.
Flow Virtual Networking is a software-defined solution that provides multitenant isolation, self-service provisioning, and IP address preservation using VPCs, subnets, and other virtual components that are separate from the physical network for Nutanix AHV hypervisor clusters.
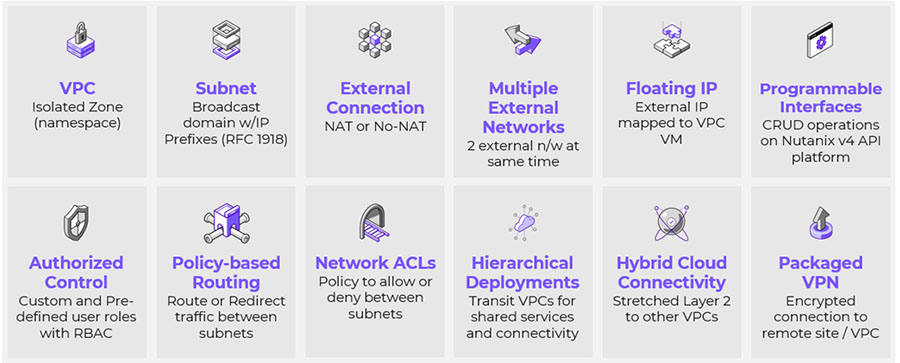
Figure 1: Nutanix Flow Virtual Networking features.
Flow Virtual Networking integrates tools to deploy networking features like VLANs, virtual private cloud (VPC), VPN, Layer 2 virtual network extension using VPN or virtual tunnel endpoint (VTEP), and BGP sessions to support flexible app-driven networking that focuses on VMs and applications.
In terms of hybrid multicloud, FVN ensures that networking remains consistent, regardless of your location. You can start to have a consistent way of networking across on-premises, hyperscalers and service providers. Your networking layer can be automated while reducing the time to provision and human errors that can occur.
For workload mobility we’ll start with the simplest use case: Connecting two sites together over a Layer 3 connection with discrete subnets on either side.
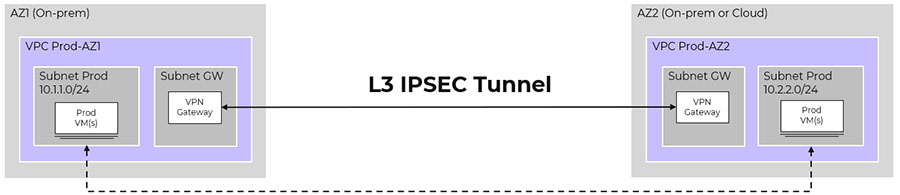
Figure 2: Layer 3 connection across Nutanix environments.
You have the option of using the built VPN gateway with Flow Virtual Networking on either side of the connection between your sites. You also have flexibility to use a physical VPN appliance at your physical site or go with a VPN option from your cloud provider.
Moving workloads over Layer 3 with different discrete subnets has the advantage of being easy to understand and route traffic. Relying on DNS makes a lot of sense with cloud-native apps that have load balancers and are dynamic in nature. Unfortunately, many legacy apps have hard-coded IP addresses to failover and usually require lots of additional steps to ensure it works.
With Nutanix disaster recovery you can failover an entire subnet, but the use-case doesn’t meet everyone's needs. Typically, customers require failover for just one part of a subnet so that workloads can continue to run on the original site. This is common in older institutions like universities, where giant address spaces make it infeasible to move everything at once.
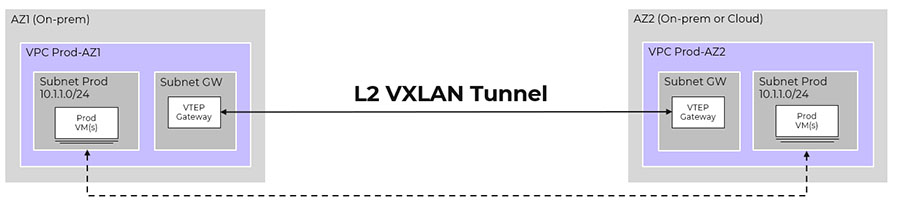
Figure 3: Subnet extension.
To overcome this challenge, Nutanix supports Layer 2 stretch, known as a subnet extension. While you can use a VPN for the connection, using VTEP is the preferred method when a VPN is already in place, which is the case in most connected environments. A VTEP reducesnetworking overhead and is the preferred method when a VPN is in place. Nutanix can provide this subnet extension with or without using flow VPCs.
Using a layer 2 subnet extension allows for partial failover and migration without having to re IP workloads. Customers do have to consider routing within their environment and how the local gateways of migrated machines will interact when moved.
One problem that can occur is asymmetric routing between your connected sites when using a subnet extension. Asymmetric routing is a situation in which packets take one path to go from source to destination, but replies take a different path to return. This is a problem when a firewall is expecting the path that traffic takes between two devices to be the same in both directions.
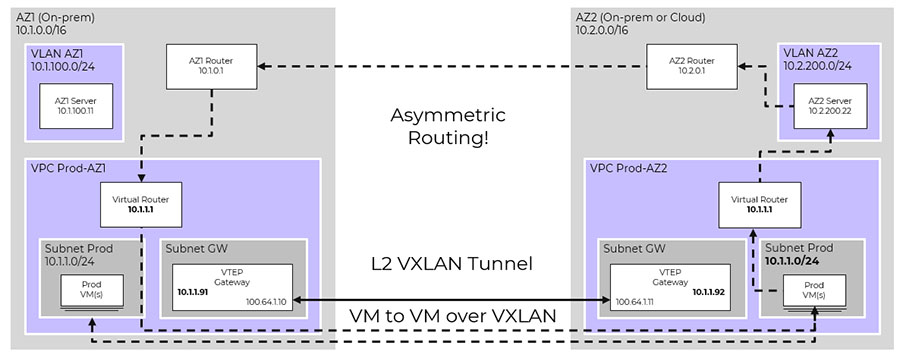
Figure 4: Asymmetric routing.
In the above diagram, we have a VM in a flow VPC in a AZ2 with a connected Layer 2 subnet extension. The VM in AZ2 in 10.1.0.0/24 wants to talk to a server in 10.2.200.0/24. The VM in AZ2 VPC has its own routing table and will have to talk to the local virtual router to make a routing decision to send it to the AZ2 server in 10.2.200.0/24. When the AZ2 server at 10.2.200.0/24 sends its response it also has its own routing table and will take a different path across the internet link. If a stateful firewall is sitting between the two sites, the firewall will only see the response back and drop the traffic.
Nutanix does have the ability to insert routes at the virtual router in Flow Virtual Networking with a new forward action in the flow VPC policy to help fix asymmetric routing. Below are available options with the new forward option.

Figure 5: Forward policy options.
This policy will override the routing action and so let's assume we applied this and are going to forward traffic to 10.1.1.91. For the source option, can we select any source or a custom source address. For the destination, you can select, external or a custom address. In both cases the external destination needs to be outside of the current flow VPC. We recommend selecting the far side of the subnet extension. In this case it will be 10.1.1.91, which is our VTEP gateway.

Figure 6: Forward policy in action.
With our forward flow policy applied, the VM in VPC Prod-AZ2 will send its traffic to the local virtual router and then the traffic will be forwarded over to the VTEP gateway in VPC Prod-AZ1. From there the traffic will go to the virtual router to make a routing decision and send the traffic to the AZ1 router. From the AZ1 router, traffic will be sent to the AZ2 server at 10.2.200.22 and be able to make the return trip back without being dropped. This is known as tromboning traffic and depending on requirements can be great to have one security appliance doing the majority of inspection. The good news is the forward action provides a lot of flexibility on how you redirect traffic.
With Flow Virtual Networking, Nutanix makes storage and networking requirements frictionless when moving workloads between different environments. There are a variety of on-demand test environments where you can see this in action for yourself. Please take a free test drive today and let us know how we can help you accelerate your business.
Diagram credit to: Jason Burns, Director, NCI Technical Marketing
© 2024 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s).