Welcome to the fourth part of our “Seven Ways to Simplify Your Digital Workspace Deployment” blog series. In the previous post, we talked about how to simplify your digital workspace solution’s virtualization and file services. We also talked about how Nutanix can eliminate the need for a SAN and how the Citrix Virtual Apps and Desktop service enables you to provide virtual apps and desktops with a flexible architecture that is always up to date. In this installment, we explore how to provide secure remote access to your end users—another key component to architecting a full workspace solution.
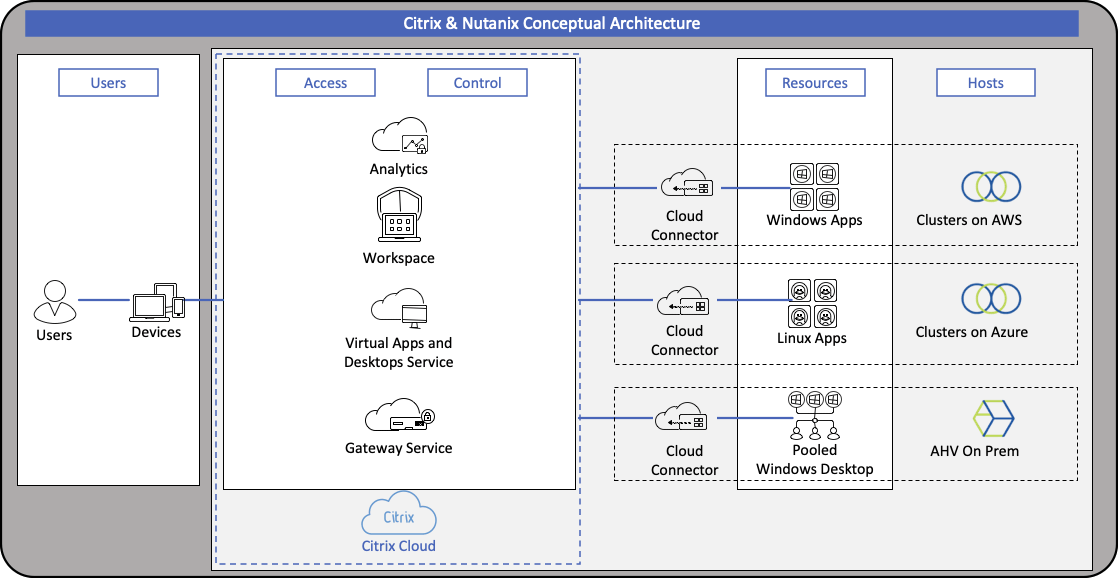
Citrix Gateway service provides secure remote access with a broad set of identity and access management options. When deploying Citrix Gateway on-premises, administrators are responsible for implementing and maintaining multiple sites, public IP addresses, network devices, and firewall rules. Citrix Gateway service hosted within Citrix Cloud removes the management overload while providing additional benefits.
With Citrix Gateway service, Citrix administers and implements the network appliances, so they always have the latest features and security patches. This also accelerates onboarding, allowing you to scale easily as you grow. Additionally, Citrix Gateway service operates in multiple PoPs around the world, which ensures high availability without administrators having to deploy additional hardware. Learn more about Citrix Gateway service.
With so many employees working remotely, security must be top of mind. So how do you provide end-users with the flexibility they need to be productive, while still securing your intellectual property? Citrix Secure Workspace Access service allows administrators to provide a complete experience. This includes giving end users single-sign-on, remote access, as well as content inspection. It allows administrators to publish SaaS applications with enhanced security policies, such as watermarking or restricted clipboard capabilities.
Last but not least, because end users use web browsers to be productive, they are vulnerable to browser-based attacks. The Citrix Secure Browser service isolates web browsing to protect the corporate network from these attacks. Deploying web browsers that are completely isolated and off the corporate network helps protect intellectual property, while providing end users with the tools they need.
All in all, Citrix Cloud services, including Citrix Virtual Apps and Desktop service, Citrix Secure Browser service, and Citrix Gateway service, remove the complexity of managing your virtual workspaces, while giving you the tools you need to provide your end users with secure remote access. Now more than ever it is crucial to have a flexible solution that allows your users to work from anywhere!
Read the previous installment, How to Simplify Digital Workspace Solution Virtualization and File Services.
Read the next series installment, How to Simplify Reporting, Analysis, and Issue Remediation.
© 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.