The cyber threat landscape is ever-changing, and organizations are moving toward the zero-trust framework to secure every part of the network. Managers and architects need more information about the network and smart recommendations to simplify the SecOps team’s workload. Traditional datacenters use firewalls to implement security checks at the perimeter to protect the network from external threats. However, they offer no protection against threats that originate from within the datacenter and spread laterally. Microsegmentation is a method of creating zones in datacenters to isolate workloads from one another and secure them individually. At Nutanix, our Flow Network Security™ solution offers a policy-driven security framework that inspects traffic within the datacenter.
With our customer-centric focus, we’ve always had a strong emphasis on making security an integral part of our design and continued innovation. Nutanix’s Security Central™ product is a security compliance management tool offered by Nutanix that simplifies enterprise microsegmentation planning and augments perimeter security across both public clouds and Nutanix on-prem. The security planning feature under Security Central has been helping virtualization admins and security managers simplify day-0 planning since its launch in 2020.
When you plan microsegmentation policies, application teams often lack the knowledge of how VMs and applications in your network are communicating with each other. In order to gather data, you reach out to other teams for help and this is a cumbersome and time-consuming process. Security Central makes your life easier by identifying related VMs and their traffic patterns so you can determine the security policies that you can apply.
Listening to our user community and their feedback, we have improved security planning to make microsegmentation planning simpler with automated policy recommendations, intelligent VM category management, and more.
Automated Policy Recommendations
The traditional way to build a microsegmentation policy is to collect traffic data with the help of other tools and teams. Then, based on this imperfect information you build a policy in monitor mode to view and observe. When you’re sure the policy is complete, you can enforce it.
The new and improved security planning capabilities in Security Central help save time and effort by auto-generating security policy recommendations. Security Central runs ML (machine learning) algorithms over the collected traffic information to suggest recommendations in the form of inbound and outbound rules for the selected set of VMs. This cuts the task of building a policy into just a few clicks without leaving Security Central.
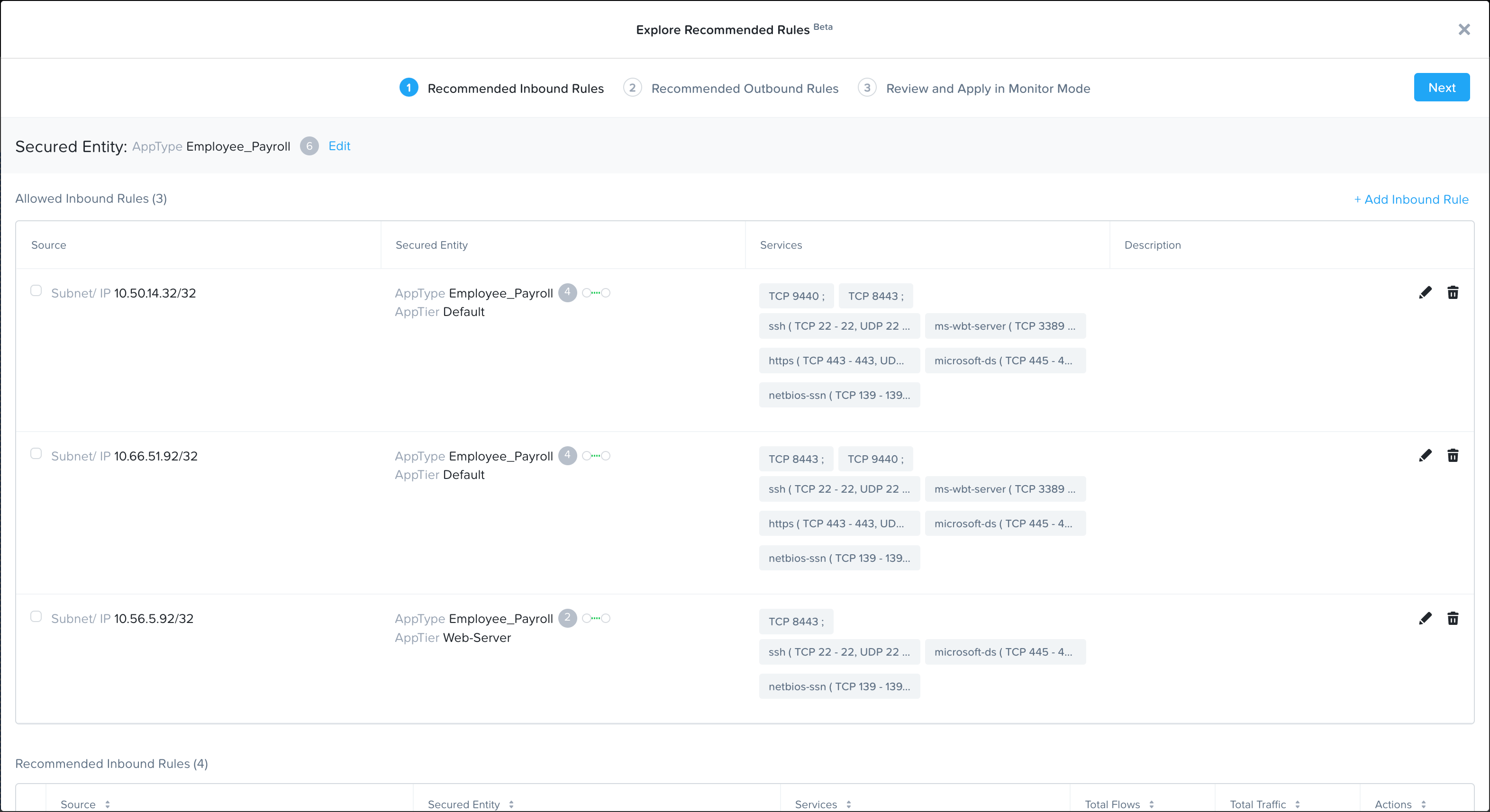
Intelligent VM Category Management
The first release of security planning simplified category management for AppType and AppTier, the primary categories of Flow Network Security. The new version of security planning builds on this foundation to allow users to create and assign any category to any VM. The intelligent ML-based suggestions from Security Central aid the decision-making process.
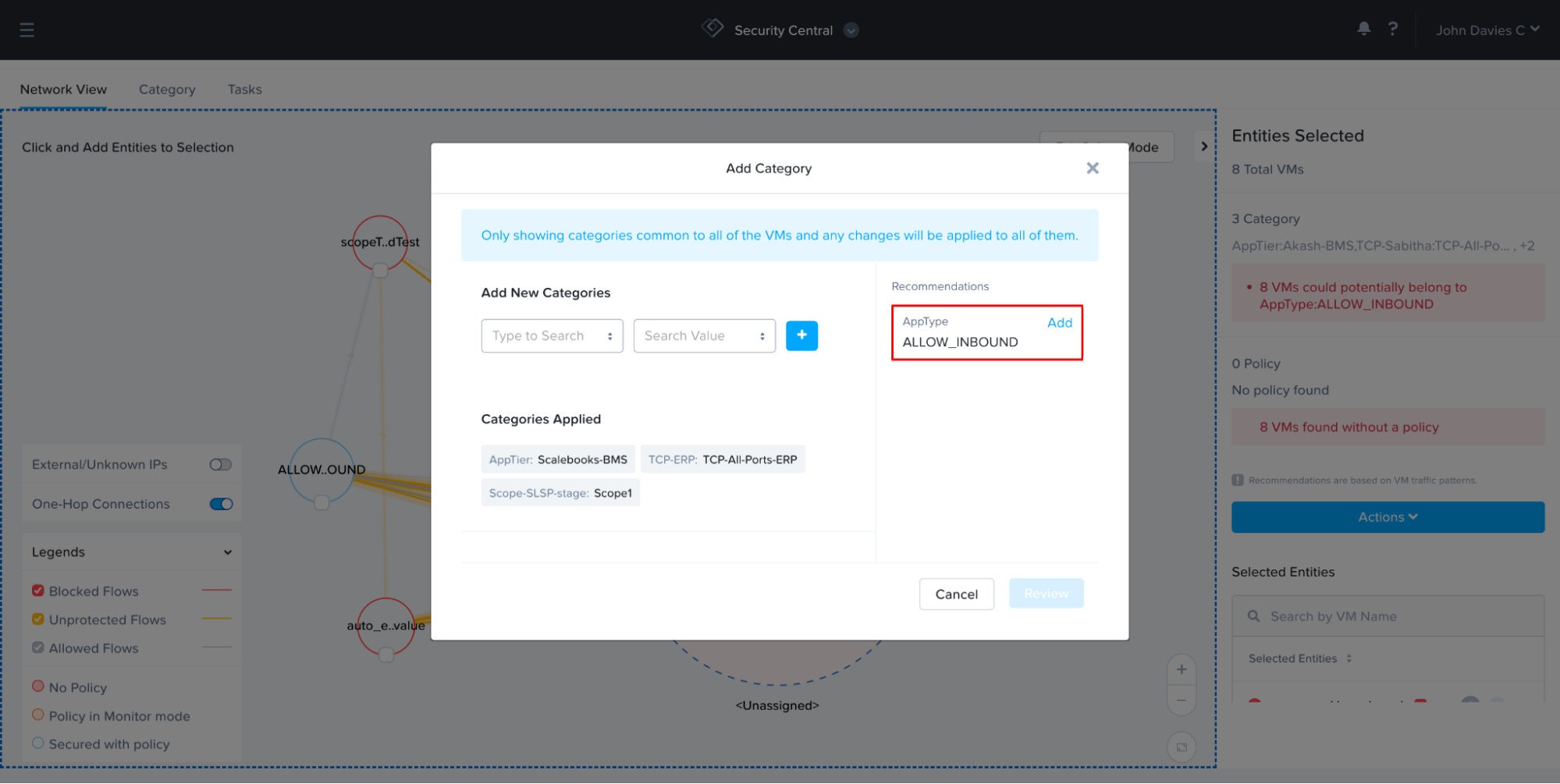
Security planning now also shows VMs that could belong to an existing category based on detected traffic. This helps organizations avoid duplicate or disorganized category creation and brings uniformity to the system.
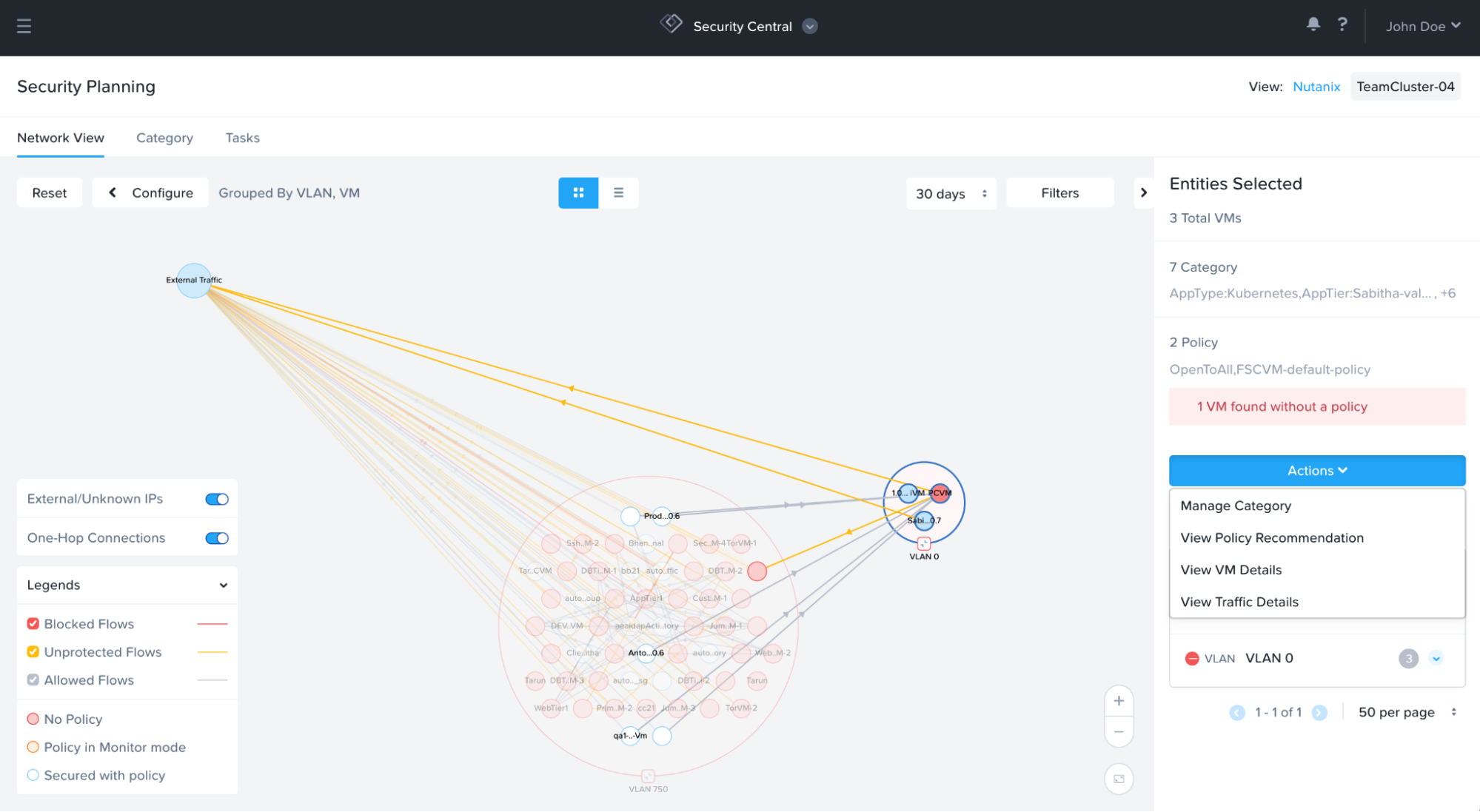
Complete Network View with One-Hop Connections
Network visualization in security planning was initially introduced to help users build trust in the system for recommended VM groupings. However, our users told us how they leverage the network view in security planning to gain valuable network traffic knowledge and perform data-driven exploration.
The new graphical network view in security planning will give a holistic view of the network with color-coded bi-directional traffic flows. If there are VMs either with or without categories in a selection, a user will see how these sets of VMs are talking to other VMs by displaying one-hop connections. A .CSV file of traffic details can be downloaded to share with other teams for analysis for a deep-dive understanding of the network.
This extensive network map with detailed information gives confidence and transparency to trust the security planning recommendations. It makes it easy to see the information these decisions are based on.
Group-Related VMs
Security Central uses ML algorithms to group-related VMs based on network traffic. In past releases, security planning only offered the grouping of VMs without AppType categories. The new and improved security planning now shows VM group suggestions for VMs that could potentially belong to an existing category or could be part of a new category.
Additionally, Security Central also identifies VM sets that can be placed in the same microsegmentation policy. For example, if you have a few VMs talking over port 3306 and there is a category “AppTier: DB-Tier” already assigned to some of these VMs, Security Central will automatically recommend “AppTier: DB-Tier” if the same communication exists between additional VMs. This makes it easy to map VMs to existing suitable categories and policies.
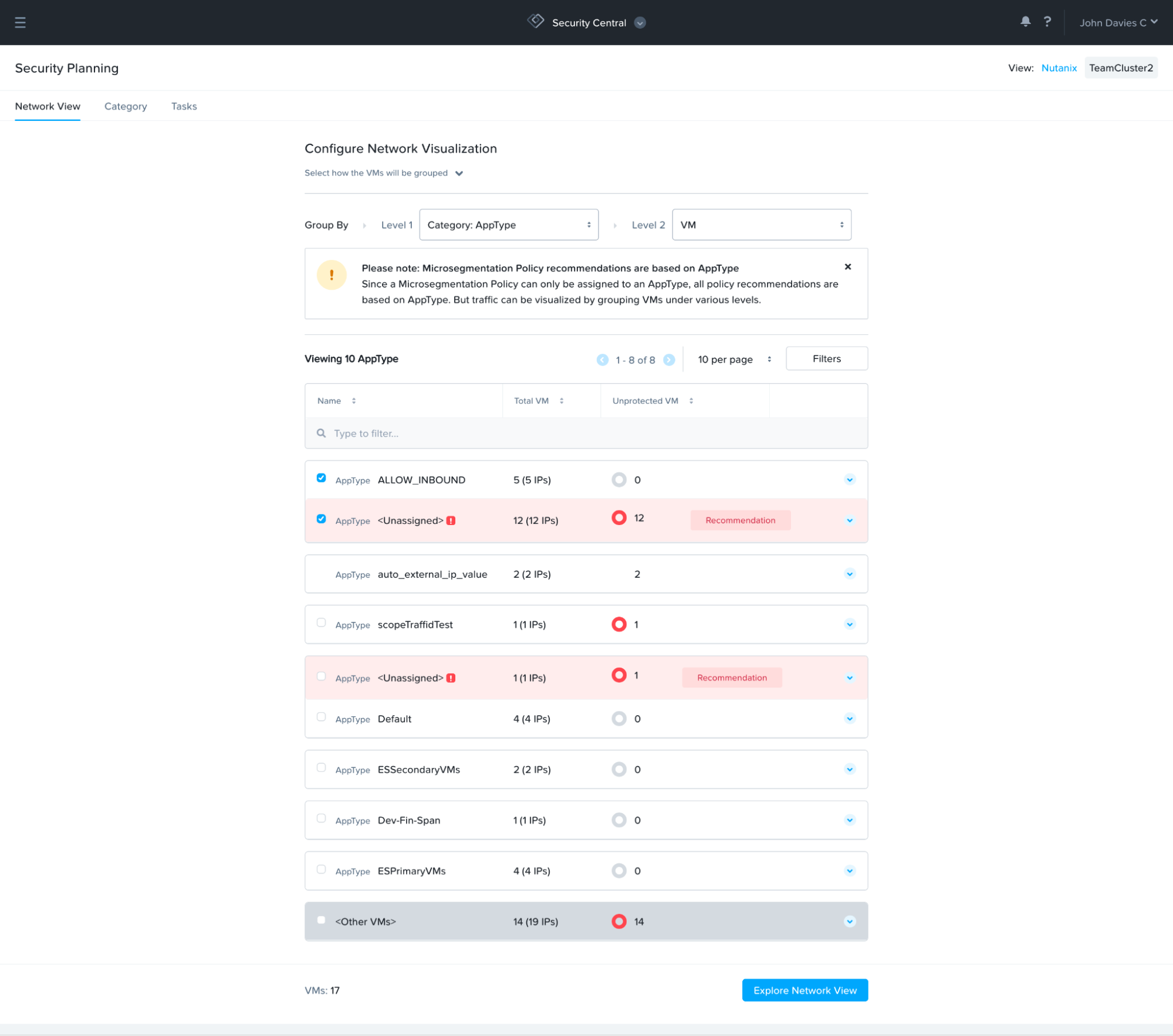
The new group-by filters empower users to build a security policy or perform network analysis with two configurable grouping tiers to inspect VM relationships by various attributes.
If you want to know more about security planning, check out the user guide. If you are not a customer yet and use Nutanix’s AHV® hypervisor, sign up today for a 60 day free trial of Security Central.
To see these updates in action then register for the webinar scheduled on March 15, 2022, at 11 AM EST, or March 15, 2022, at 9 AM CET.
© 2022 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.