Nutanix Frame™ Desktop as a Service (DaaS) solution supports multiple networking models. One of the more popular networking models for enterprises is the Frame Private networking model. This model allows the Frame workload VMs to have private IP addresses on the enterprise private network and access private networking resources and it is the simplest way to inherit existing network security processes.
However, remote users still need a way to connect to these private networks. The traditional way of implementing this access is to deploy a VPN, but that requires implementing and maintaining software on the user endpoint devices and VPN connections can overload security products like firewalls.
Frame offers a Streaming Gateway Appliance (SGA) to meet this need, but some enterprises may wish to take advantage of the “security as a service” model offered by Zscaler, Inc. Zscaler offers a “DMZ as a service” solution that can provide DMZ type functionality without the complication involved in many DMZ deployments. The Zscaler® service maintains many certifications required by government agencies and it meets the rigorous standards required by the most security conscious organizations.
In this blog you will learn how Zscaler Private Access (ZPA) and Frame DaaS can work together to provide a remote access solution to a private cloud with a simplified administrative model while maintaining a high level of security.
Architecture
Below is an example of a Frame Private networking architecture deployed with a Streaming Gateway Appliance (SGA).
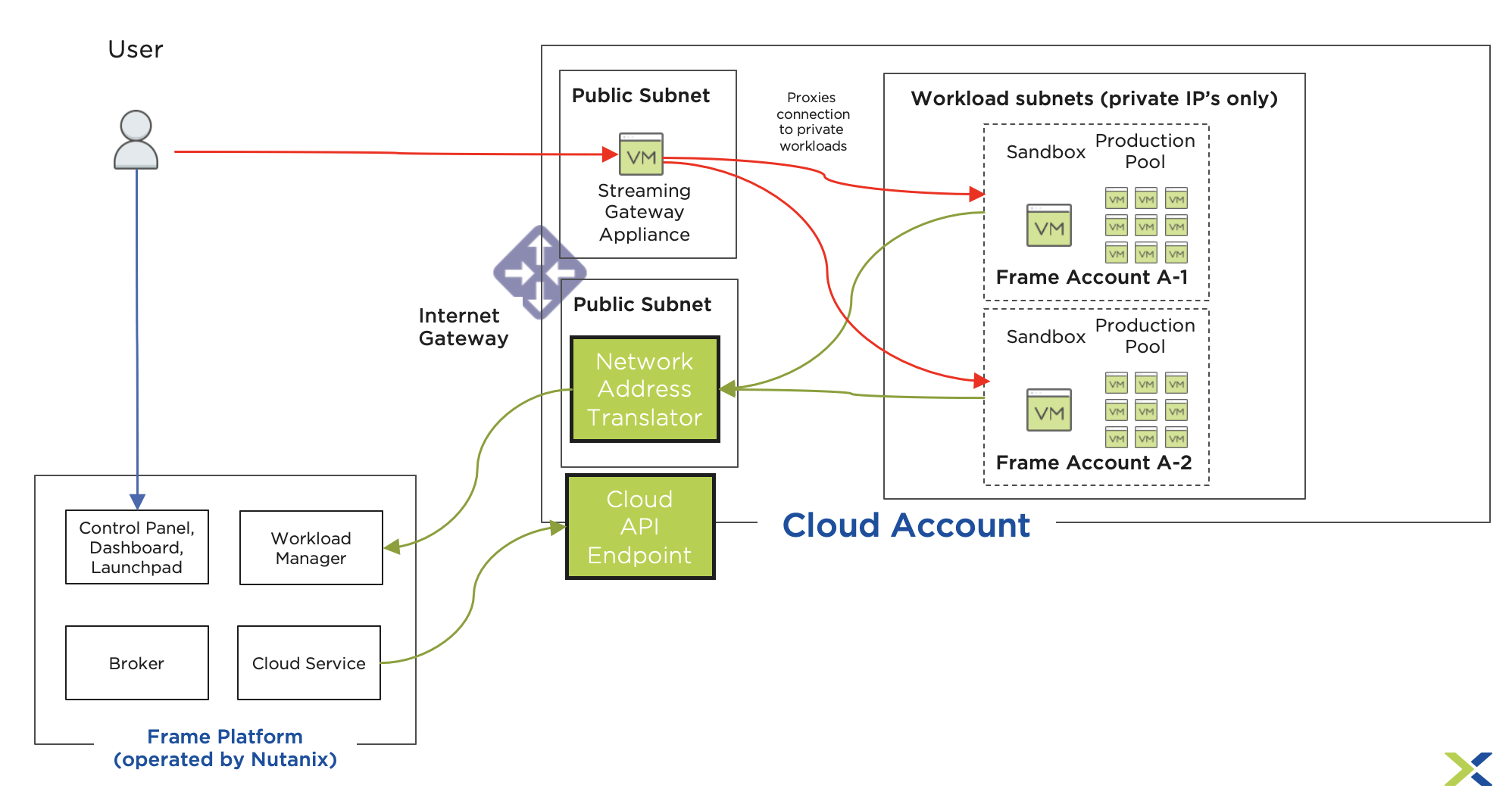
Frame with SGA Architecture
In this Architecture, all the workload subnets only use private IP addressing. The Frame DAAS platform orchestrates the workloads via calls to the Cloud Provider’s public API endpoint and communicates with the workloads via an internally initiated connection through an outbound only NAT GW (the green lines on the diagram). The end user authenticates with Frame (the blue line) and then is presented with the desktops and applications to which they have access. When they click on an icon a session is started and the user is redirected to the workload via the SGA appliance, which proxies the session into the appropriate workload (the red lines). In many enterprises, the SGA and the NAT GW sit in a Demilitarized Zone (DMZ) that has a high level of security and monitoring capabilities due to the need to connect directly to the internet.
The Zscaler architecture is similar, but does not require the enterprise to deploy a DMZ for the SGA. Instead, the inbound public connectivity is managed by Zscaler and the private network does not need to allow any inbound connectivity, which simplifies the security model. The Frame platform will still need to connect to the Cloud Providers API, but those endpoints are already public and managed by the cloud provider and some sort of outbound NAT GW will be needed to allow the workloads to talk to the frame platform.
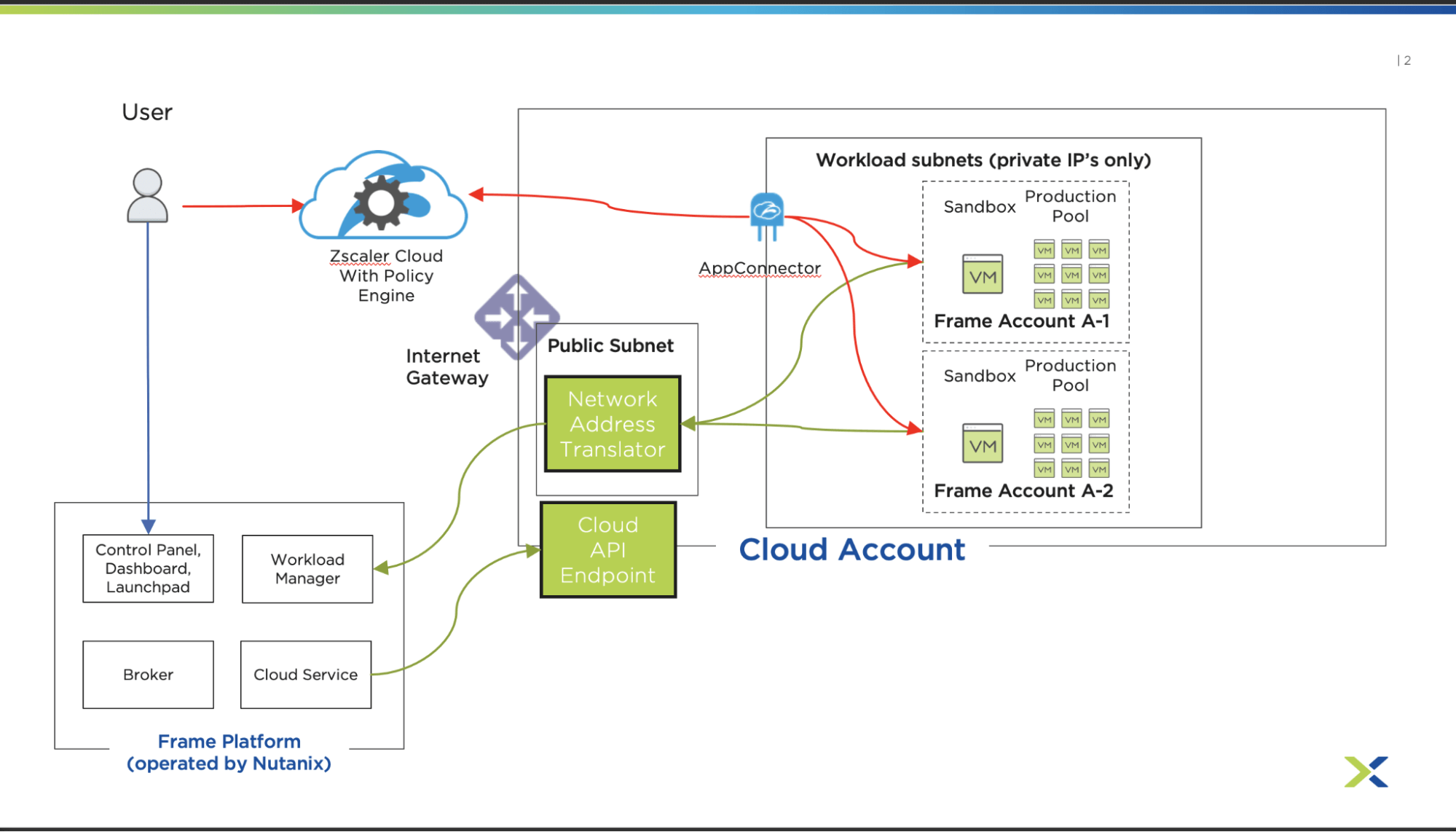
Frame with Zscaler Architecture
Setup Frame Private Networking
For the Frame portion of this architecture, you will need to set up a Frame account with Private networking. This setup will use your existing cloud service to set up a private network for Frame workloads. The Zscaler AppConnector appliance will also need to be deployed in a VPC or subnet that has access (at least over TCP port 443) to the private subnets where the workloads will be deployed.
Zscaler Private Access setup
The high level steps for setting Zscaler Private Access (ZPA) to work with Frame are:
Define the Frame Application Segment
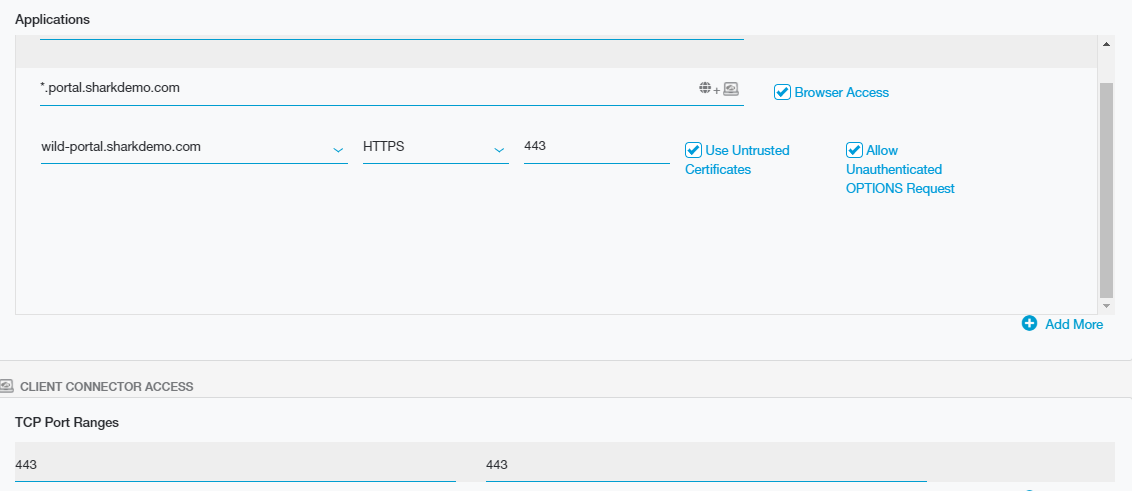
Define the application segment
*.portal.sharkdemo.com is the application segment defined in this example – any requests matching this wildcard domain will be associated with the Nutanix Frame application and serviced by ZPA.
Browser Access mode is selected for this application segment and the X.509 Certificate wild-portal.sharkdemo.com was created and associated with this App Segment.
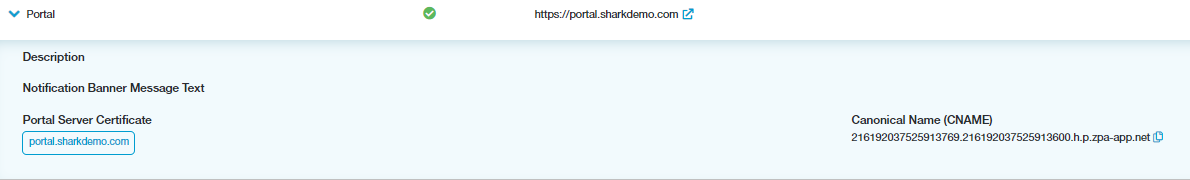
Associate the certificate
Browser Access mode allows a client to use a generic web browser to access this Frame application without the need to install the Zscaler Client Connector on the endpoint. This means that a public DNS CNAME must be created to map *.portal.sharkdemo.com to the Zscaler Private Access cloud.

Wildcard CNAME record
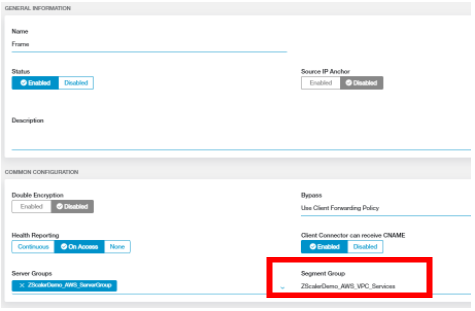
Next, we associate the server group (for load distribution and health monitoring) and application segment group (for policy) with this Application Segment. An AppConnector was previously created (outside the scope of this document) and associated with this server group.
Access Policy
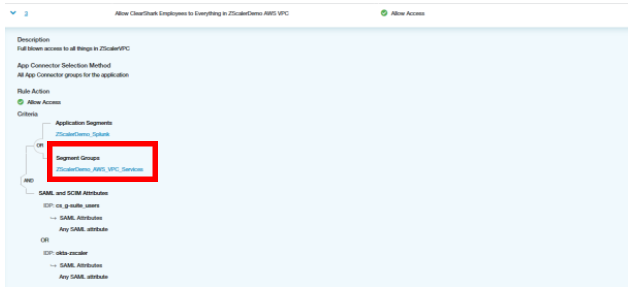
An access policy was created to allow access to the Frame application. In this case, an allow policy was created that granted access to the Application Segment group (ZScalerDemo_AWS_VPC_Services) that the Frame application segment is associated with.
Access Policy
Now, if a user opens a web browser and types in the URL .portal.sharkdemo.com it will resolve to the “exporter” component of the ZPA cloud service:
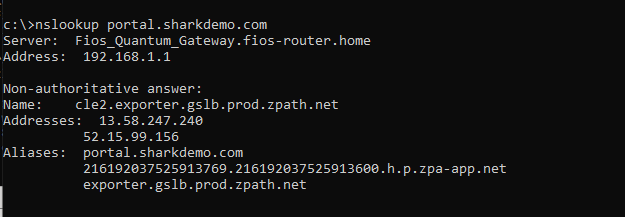
Verify DNS
User Portal
For ease of use, a user portal was created which will have a direct link to the Frame DaaS application. A user portal allows the actual Frame link to be private and allows for other associated applications to be made available to the user community.

Define User Portal
The details of the Frame instance on the user portal is shown below…

Define User Portal
Additional configuration needed to support the Frame service from Browser Access Mode. (Will need to be configured by Zscaler Support)
POST: /zpn/api/v1/admin/configOverrides
Request Body:
{
"configKey": "config.feature.samesite_none",
"configValue": "enabled",
"configValueInt": 1,
"customerId": ***,
"targetGid": ***,
"targetType": "customer"
}
POST: /zpn/api/v1/admin/configOverrides
Request Body:
{
“configKey”: “config.feature.cors_enabled”,
“configValue”: “enabled”,
“configValueInt”: 1,
“customerId”: ,
“targetGid”: ,
“targetType”: “customer”
}
Private DNS
To make sure the connections get routed properly, the Zscaler AppConnector will need to be able to resolve the DNS names that Frame uses to the appropriate workload IP. To do this, create a host file on the AppConnector virtual Appliance that has an entry for all possible private IP addresses that points to . (e.g., 10-0-100-50.portal.sharkdemo.com needs a local host entry pointed to 10.0.100.50)
Finalize Frame Configuration
Now you will need to contact the Frame support team and indicate that you need to change your Frame account to support a “Custom base domain name”. You will provide the Frame account name and the DNS domain you are using on your ZPA (in this example *.portal.sharkdemo.com). The Frame support team will be able to update your Frame account to use that domain. When your users launch a virtualized application or desktop, Frame will direct the users to the workloads using the custom domain.
End User Experience
To access their virtualized applications and/or desktops, the end user starts by connecting to the Zscaler portal https://portal.sharkdemo.com
Where they will need to logon with their Zscaler username
Portal Login
The user will be redirected the third-party identity provider configured within Zscaler.
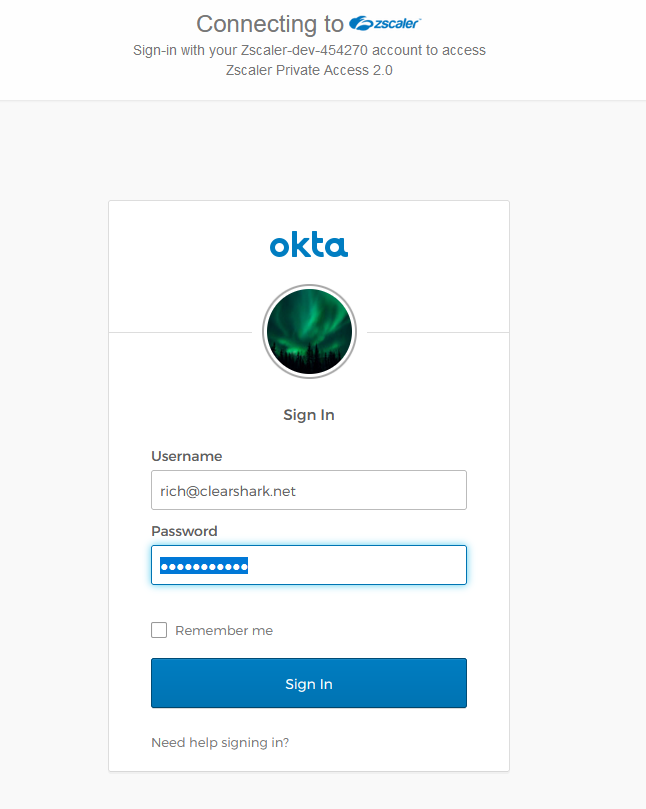
Identity provider login
Once authenticated, you’ll be redirected to the ZPA User Portal
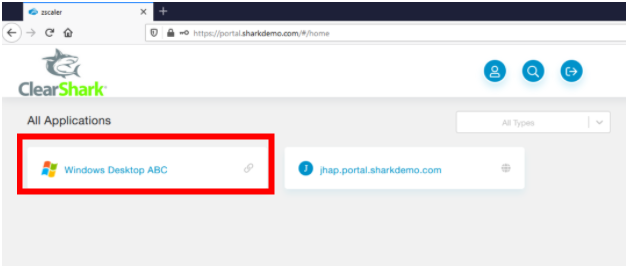
ZPA User Portal
Select the Nutanix Frame application - Windows Desktop ABC
This will direct the user to the Nutanix Frame Launchpad. Nutanix Frame will redirect the user to the third-party identity provider configured for user authentication.

Connect to Frame Launchpad
Use your Frame credentials to log into the DaaS instance.
Wait as the DaaS instance spins up on the backend (could take a minute).
Loading Desktop
Your Desktop as a Service instance will appear…
Frame Session
Conclusion
Combining Zscaler’s “security as a service” products with Frame DaaS allows enterprises to leverage leading “as a service” products to deliver a secure, performant, desktop experience to any user with a browser. By using a Zscaler AppConnector service, it does not require that the customer setup and maintain a DMZ or a Streaming Gateway Appliance, easing the overall administrative experience. Zscaler also provides additional protection of important corporate data resources by ensuring that the corporate data never leaves the private network except through approved security processes.
David Horvath is a Senior Solutions Architect with Nutanix Frame. He has been a part of the Frame team for almost 5 years and prior to that spent 20 years consulting on various Information Technology projects with the US Intelligence Community.
Rich Johnson is a senior solutions engineer with Zscaler Technology. He has spent the past 30 years working in the networking and computer security industry supporting the US Department of Defense.
James Happel is a Systems Engineer with ClearShark. He has been with ClearShark for almost 3 years and prior to that spent 15 years working on various projects with the US Department of Defense.
© 2021 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not been independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.