Engineered Differently
Built-in Security Across Platform, Data, Network and Applications
By Jason Burns and Eric Walters
So far in 2025, enterprises have faced a surge in sophisticated cyberattacks — with ransomware, data breaches, and social engineering attacks dominating the threat landscape. AI is playing an increasing role in attacks. Almost 9 in 10 global organizations (87%) faced an AI-powered cyber attack in the last year. Recent cuts in funding for the Cybersecurity and Infrastructure Security Agency (CISA) may add to the cyber risks that enterprises face.
With this as a backdrop, enterprises are looking for ways they can shore up security and increase cyber-resilience. However, the landscape of security and resilience solutions is complex, and some IT vendors still treat security as an add-on rather than building it into their solutions.
The Nutanix Difference
At Nutanix, security is built in, not bolted on. By designing in security at every level—platform, data, network, and application—Nutanix Cloud Platform lets you protect your apps and data against cyber attacks and data loss.
Nutanix helps you provide security everywhere while minimizing the complexity of security operations. In a recent survey of Nutanix customers, IDC found that switching to Nutanix Cloud Platform made IT security teams 32% more efficient.
At Nutanix, it’s all about providing layers of protection, starting with hardened infrastructure, adding in virtual networks, VPCs and microsegmentation—all complemented with advanced data protection and rapid recovery. The sections that follow detail how Nutanix goes above and beyond to deliver security at the platform, data, network, and application layers.

Platform
When it comes to platform security, enterprises need infrastructure that’s secure out of the box. If your team has to take extra manual steps to ensure security every time you deploy a new server, that’s a disaster waiting to happen. Nutanix relies on a number of built-in technologies to protect its platform:
- Self-healing STIG: Nutanix has its own security hardening guides—based on the US Department of Defense (DOD) Security Technical Implementation Guide (STIG) frameworks—that are easy to maintain and machine-readable. Nutanix software automatically configures itself based on this STIG, an approach that allows infrastructure to be secure out of the box. The system performs regular health checks, and if a system is no longer compliant, the STIG is reapplied, to reduce the risk of manual misconfigurations and configuration drift.
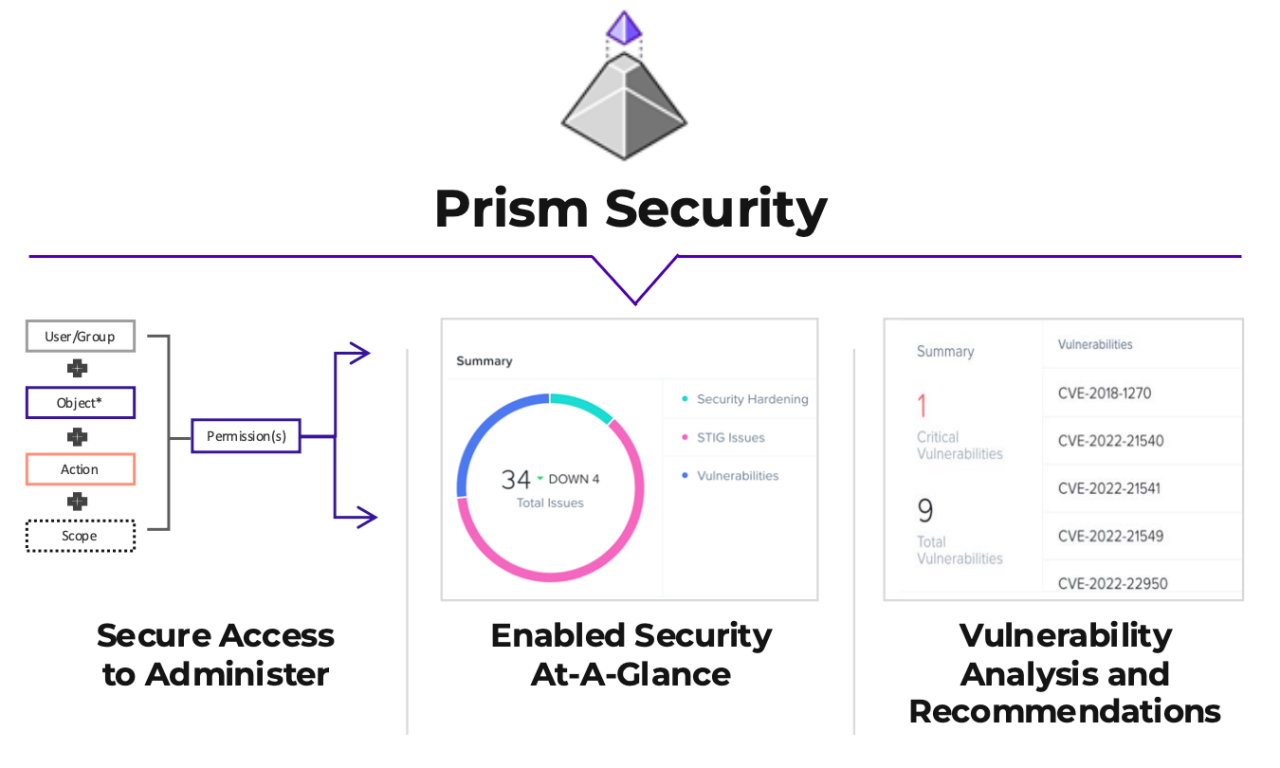
- Security Dashboard: Nutanix platform security is built on rigorous authentication, role-based access control, and auditing, with everything built into a customizable security dashboard that is part of Prism Central, enabling administrators to easily visualize and drill down on issues, see the upgrade status of all servers, the STIG status across all servers, network security policies, and more.
- Zero Trust: Nutanix embraces zero trust security, offering a range of solutions—including microsegmentation, least privilege access, and continuous authentication—that help teams to reduce the attack surface, address compliance regulations, and efficiently respond to and prevent unauthorized access, insider threats, lateral movement by attackers, and data exfiltration.
- Vulnerabilities and upgrades: In some enterprise IT environments, the biggest security risk is failure to keep up with security-critical software upgrades. The Nutanix Vulnerability Database allows you to see the status of published vulnerabilities so you can take action. Nutanix Life Cycle Manager (LCM) takes the pain out of upgrading Nutanix software and firmware with comprehensive dependency management. LCM does the hard work of managing all upgrade dependencies and simplifies upgrade planning and scheduling with 1-click simplicity.
With traditional infrastructure, staff would spend about 50% of their time on management. Thanks to Nutanix, the same team now saves 3–4 hours per month each, especially due to easier software upgrade processes.
The video below discusses many of the Nutanix platform security features and other features described in this blog.

Data
To help protect data security and data resilience, encryption combined with business continuity and disaster recovery (BCDR) features have become essential. Nutanix differentiates itself from the competition with solutions that deliver this functionality while making these features easy to use.
- Flexible data-at-rest encryption: Encryption helps prevent data loss or theft and is often a requirement to comply with industry regulations such as HIPAA and PCI-DSS. Nutanix supports software-based encryption and hardware-accelerated options using self-encrypting drives (SEDs) that automatically encrypt data, providing security without performance loss. You can also choose between our native key management server (KMS) or external key managers. The ability to configure encryption at the cluster, container, or policy level provides granular control while minimizing performance impacts and keeping operations simple.
- Business continuity and disaster recovery: BCDR is a critical part of data resilience. Nutanix offers a range of native data protection and disaster recovery capabilities, including:
- Async, Near-Sync, and Synchronous replication
- Secure, immutable snapshots
- Multcloud Snapshot Technology (MST) providing snapshots to the cloud or an S3 object store
Nutanix provides strong protection across all RPO and RTO levels, and you don’t need to purchase additional tooling to do site recovery, including recovery to the cloud. By using Nutanix capabilities in place of third-party or application-specific capabilities, you can provide data protection and online DR for the applications in your portfolio with ease and cost efficiency.
- Global visibility and frontline defense: Advanced protection for file and object data is provided by the Nutanix Data Lens solution. Proactive identification of threats and actionable insights elevate your data security posture. Nutanix Data Lens helps you assess and mitigate data security risks by identifying anomalous activity, auditing user behavior, assessing file permissions and calculating a risk score, adhering to monitoring requirements, and enabling guided recovery in the event of an attack.

Understanding access to our data is very important for us to ensure data is secure, safe, and being used properly. Tools like Data Lens give us the insights we need to understand who is accessing our data, if it’s appropriate access, or if there is an attempt to misuse or attack our data. The forensics and the new permissions and access risk views are important tools to keep our data safe from malicious users, or from threats such as ransomware.
To learn more about Data Lens, watch the following video:

Network
Network security is arguably the hardest part of the security stack to get right. Nutanix differentiates itself with centralized management, seamless hybrid multicloud support, and simple deployment.
- Software-defined networking: Nutanix Flow Virtual Networking automates the deployment and management of SDN infrastructure for your Nutanix environment, bringing virtual private cloud (VPC) and other advanced virtual networking constructs together to bridge traditional and cloud native network models. Our software-defined approach simplifies infrastructure and removes the need for costly hardware segmentation solutions or more complex and static physical network architectures.

- Network security: The Nutanix Flow Network Security solution delivers microsegmentation for zero-trust security in hybrid multicloud environments, providing granular, policy-based network isolation to secure workloads and prevent lateral attacks. Flow uses distributed firewalls to enforce policies at the VM or container level, while providing centralized management and visibility. It also supports flexible segmentation, dynamic policy updates, and integration with identity providers for secure access control. The lightweight architecture of Flow minimizes latency, delivering critical performance for edge, datacenter, and Nutanix Cloud Clusters deployments.

Centralized monitoring and management: The Security Central solution, part of the Nutanix Cloud Manager (NCM) suite, is a cloud-based SaaS platform providing centralized security monitoring and compliance support for hybrid multicloud environments. It offers real-time visibility into security posture, identifying vulnerabilities, misconfigurations, and threats across Nutanix clusters, VMs, and public clouds like AWS, Azure, and Google Cloud. Security Central provides valuable information for environments subject to compliance audits, aligning with standards like NIST and PCI-DSS, and delivers actionable insights through a unified dashboard. The software integrates with Flow Network Security for microsegmentation and policy enforcement.

Application
At Nutanix, we believe the keys to achieving application-level security are consistent deployments and upgrades combined with deep packet inspection, and we’ve developed innovative tools to help you deliver that.
- Database consistency: The Nutanix Database Service (NDB) framework delivers consistent database deployments to support application needs by automating database provisioning, cloning, and patching across Nutanix hybrid multicloud environments. NDB applies Nutanix and database engine best practices so that configurations are both uniform and secure.
- App deployment: For applications and application components, you can streamline deployment using our NCM Self-Service solution, which provides consistent application deployments through automated blueprints. Blueprints can be created via a user-friendly UI or Python-based scripting for flexibility. They can encapsulate VMs, containers, or applications, and they can be published directly to end users through the Nutanix Marketplace for self-service access.
- Consistent cloud native deployment: As your operations increase reliance on containers, our Nutanix Kubernetes Platform (NKP) software can provide for the security and consistency of Kubernetes and cloud native applications.
NKP exceeds NSA/CISA Kubernetes security hardening guidelines and can be configured to meet defined security standards. It also features built-in security capabilities, including RBAC, encryption, and continuous monitoring, and it simplifies full air-gapped deployments.
NKP provides consistent Kubernetes deployments using declarative automation, CNCF-compliant clusters, and standardized blueprints. A unified, CNCF-compliant Kubernetes stack enables consistent application deployments.

- Deep packet inspection: A final element of application security is deep network packet inspection, which looks into the application layer of network packets. Nutanix makes it easy to provide deep packet inspection with traffic partners such as CheckPoint, Palo Alto Networks, Fortinet, and Cisco. Nutanix has cultivated an ecosystem of security partners that enable you to preserve and extend your existing security investments.
Ensuring high levels of security is a key requirement for government implementations, and GDIT is able to provide first-class support for air-gapped environments to its military clients via NKP.
Read the case study.
How Nutanix Security Stacks Up to VMware
Before we close, it’s worth considering how Nutanix security stacks up to VMware offerings:
- Platform: The Nutanix STIG is built-in to every system. STIGs are available for VMware products, but they are separate. This means they must be applied either manually or through automation to achieve security. Nutanix works hard to make upgrade status clear and upgrades simple, with easy and efficient GUI-based, 1-click, full-stack upgrades. The vSphere Upgrade Options guide outlines a 7-step process for upgrading vSphere, including separate steps for upgrading vCenter, ESXi hosts, and VMs with references to separate guides for each..
- Data: Nutanix Data Lens provides active data defense. VMware uses a suite of products to provide cyber protection and recovery, which may add complexity and cost.
- Network: Nutanix Flow networking capabilities are available with all NCI subscription levels except Starter. VMware no longer offers standalone licenses for NSX; VMware’s software-defined networking capabilities (NSX) are available with VMware Cloud Foundation (VCF).
- Application: Nutanix Cloud Manager Self-Service capabilities are available with all NCM subscription levels except Starter. VMware self-service capabilities are available with VCF and provided by VMware Aria Automation (recently rebranded as VCF Automation).
In our next post, we’ll explore how Nutanix delivers zero-touch provisioning, configuration management, and software updates at massive scale.
Have questions or insights? Feel free to reach out—we’d love to hear how your team is tackling hybrid multicloud complexity.
Explore the IDC study to see how Nutanix customers are cutting costs and boosting efficiency. Or discover how Nutanix can simplify and de-risk your migration with a free Test Drive. See firsthand how your workloads run on our platform and plan your move with less complexity and more confidence.
In case you missed it, view the first blog of the Engineered Differently series, “Nutanix Delivers a Uniform Experience Across Datacenter, Edge and Cloud.”
©2025 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product and service names mentioned are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. Nutanix, Inc. is not affiliated with VMware by Broadcom or Broadcom. VMware and the VMware product names recited herein are registered or unregistered trademarks of Broadcom in the United States and/or other countries. All other brand names mentioned are for identification purposes only and may be the trademarks of their respective holder(s). Customer statements on results, benefits, savings or other outcomes depend on a variety of factors including their use case, individual requirements, and operating environments, and should not be construed to be a promise or obligation to deliver specific outcomes