Email. Movies. Files and records. Where do they exist? On the phone? Laptops? Web servers? The probable answer – as of today – is, the cloud.
As technology has progressed, the storage, access, and transfer of data has become increasingly abstract to the user. Moving from the individual to the organizational level, this abstraction turns out to be all the more pertinent, as devices and interfaces continue to change dramatically with evolving consumer and user needs.
Enter virtualization – the creation of a “virtual” hardware or software resource, be it a server, workstation, operating system, storage device, or network. Virtualization transforms the traditional computing system by consolidating multiple workloads and environments into a unified system.
Essentially, virtualization changes the way of looking at the underlying technology from physical to logical. Regardless of the number of devices or capabilities of the physical hardware involved, they are all partitioned into virtual machines (VMs), each with its own OS and set of functionalities, as and when computational, data access or storage, or transactional needs arise in a particular workload.
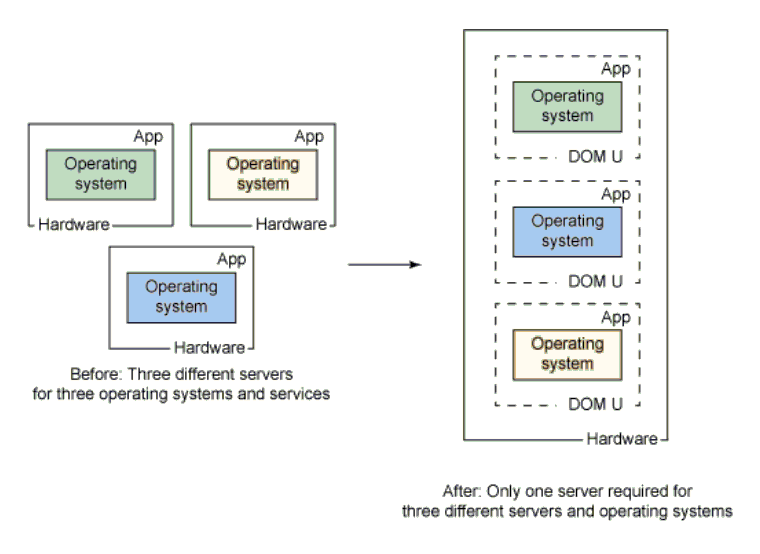
Source: IBM
What Is a Hypervisor and How Does It Work?
What makes virtualization possible is a piece of software (or firmware or hardware in some cases) called a hypervisor. It performs the “abstraction” or divvying up of hardware or OS resources into VMs, so that each VM has a specific set of capabilities such as memory, storage, CPU power, and network bandwidth. These VMs are created, destroyed, stopped, started, and used according to the needs of the application or workload for which they are allocated. Unsurprisingly, hypervisors are also called Virtual Machine Monitors (VMMs).
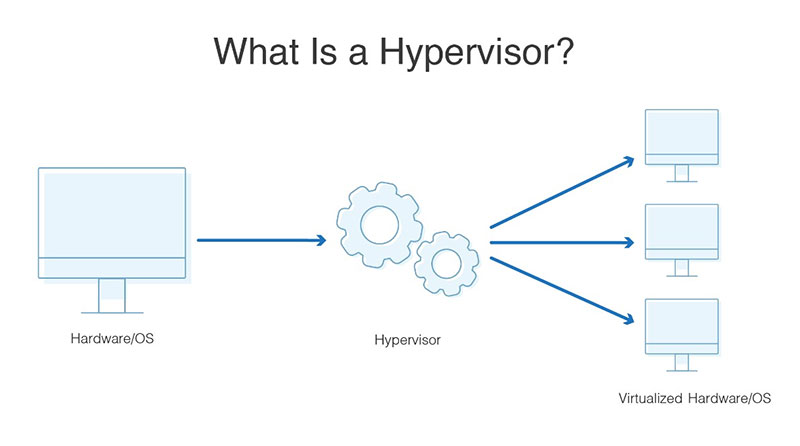
Source: DNS Stuff
Other than partitioning, a key function of the hypervisor is isolating the VMs from each other, so that one VM isn’t affected by a problem in another. The hypervisor also handles communication between VMs and applications running on different VMs. Finally, it enables redundancy and replication for load balancing, backup, and disaster recovery.
A hypervisor is composed of three main modules that work in conjunction with each other to emulate the underlying hardware:
- Dispatcher: Reroutes the instructions from the VM instance to one of the other two modules, depending on the type of request
- Allocator: Decides and allocates the system resources that the VM needs to be provided in real-time
- Interpreter: Consists of routines that are executed when the VM sends privileged instructions
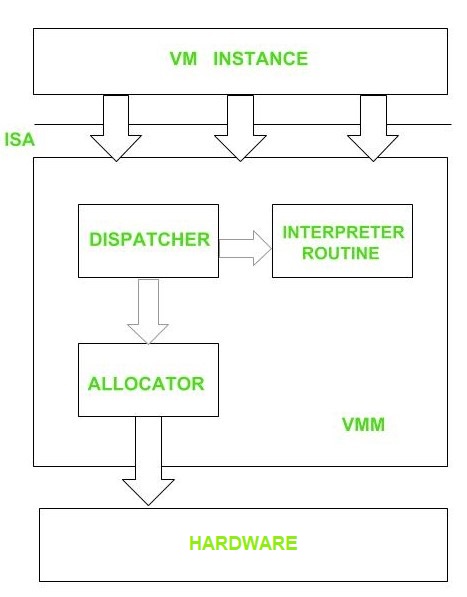
Source: GeeksforGeeks
The Need for Hypervisors
Hypervisors have been around for a long time. They were developed in the 1960s and 70s by IBM and originally designed to run applications over OS-level virtualization as well as test new hardware concepts without jeopardizing the main production system – the whole ecosystem ran inside a mainframe at the time. The term hypervisor denotes a program that controls supervisors, which is the traditional term for the kernel of an operating system.
Hypervisors and VMs are essential for a lot of present-day IT-related tasks, including server and datacenter management, building public, private, and hybrid cloud environments, desktop virtualization, or simply running an application that’s not compatible with the current OS on a particular system.
An IT infrastructure that operates multiple servers running different OSes, and yet running a set of applications or services for users located all over the world is difficult to partition and manage. A hypervisor enables consolidation of these displaced resources and virtualize them into a centrally managed pool, so that the sum of all resources can be efficiently allocated and used. Virtual resources can also be replicated in parts, in order to balance utilization and redundancy.
Types of Hypervisors
Hypervisors fall into two main categories, based on the level of interfacing they do. The underlying system on top of which the hypervisor is installed is called the “host” while the VMs it creates and manages are called “guests.”
Type 1 / Native / Bare Metal Hypervisors: A Type 1 hypervisor is one that’s installed directly on the physical hardware, without an OS in between, giving rise to the name “bare metal” hypervisor. It acts as an OS itself with direct access to the hardware, and therefore, doesn’t have to rely on device drivers or other firmware.
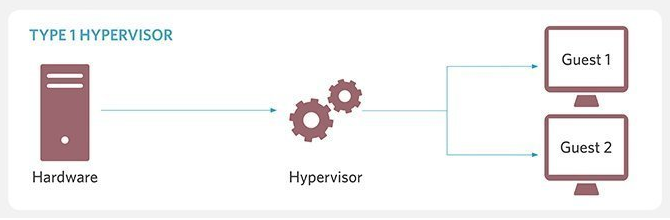
Source: TechTarget
Needless to say, Type 1 hypervisors offer high performance in terms of compute power and are scalable to the limit of the hardware, making them excellent choices for enterprise or datacenter computing. They also allow direct optimization of the hardware and give administrators the ability to manually or dynamically allocate resources. This saves organizations from having to buy separate servers or private cloud services for different applications.
Type 1 hypervisors are highly secure because they don’t present a large number of touchpoints for attackers to exploit unlike OSes. Every guest VM is logically isolated against malicious software or attacks.
Type 1 Hypervisor Vendors – VMware vSphere ESXi, Microsoft Hyper-V, Citrix Hypervisor, Nutanix AHV
Type 2 / Hosted / Embedded Hypervisors: A Type 2 hypervisor is “hosted” on top of an OS that is installed on the host machine. Since it is built and runs as an application on the OS, the Type 2 hypervisor cannot make direct calls to the memory, CPU, storage, or network hardware. This creates more latency in the system compared to Type 1 hypervisors. It also makes them vulnerable to any security flaws in the underlying OS.
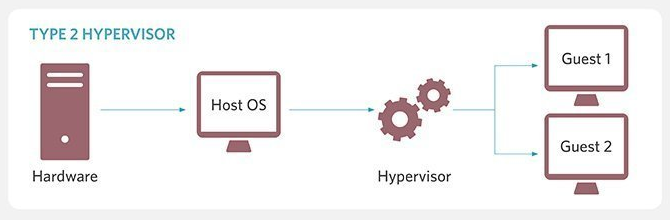
Source: TechTarget
Type 2 hypervisors originated from x86 virtualization programs that deployed VM software on top of existing OSes. Hence, they are more common in personal computing or client workstation scenarios. At the organizational level, they may be used for functions such as software testing, where performance and security are of less concern.
Another group classified as “embedded” hypervisors also falls within the Type 2 category – these are hypervisors for embedded systems with real-time OSes which don’t need full virtualization, but have limits on memory, power, and overhead. Although these devices are more robust, there is less standardization in hardware and software systems, with a wide variety of architectures in use. This means embedded hypervisors need greater control over information flow.
Kernel-based Virtual Machine (KVM)
KVM is a unique and popular open-source hypervisor built into Linux distributions that allows creations of VMs on the Linux OS. It has characteristics of both Type 1 and Type 2 hypervisors. Since KVM is a kernel module of Linux, it converts the host OS itself into a bare metal Type 1 hypervisor. On the other hand, it is part of the code that interacts with other applications, which can compete with other kernel modules for resources, giving the installation some characteristics of Type 2.
KVM offers all the hardware, compute, and storage support of Type 1 hypervisors, including live migration of VMs, scalability, scheduling, and low latency. VMs created with KVM are empirically known to be secure.
Hardware Acceleration
Many manufacturers tweak their devices to provide extra support for hypervisors by building in hardware acceleration technology, which speeds up tasks related to virtualization. Intel and AMD, for example, add support for nested virtualization and extensions that enable second-level address translation.
These extensions perform process-intensive tasks that are central to creating and managing virtual resources. Without these assists, the hypervisor would need to handle these tasks with software instructions, which would limit performance as well as the number of VMs that can be created by the system.
Since Type 1 hypervisors are more common in the enterprise, where hardware and software are typically used as a combined and managed solution for specific workloads, they are built to even rely on hardware acceleration support, which is usually enabled through the system’s BIOS. On the other hand, Type 2 hypervisors are capable of taking advantage of native hardware acceleration, but substitute for these tasks via software emulation if the necessary features or support aren’t available.
Hypervisor Capability Expansion
Today, there are a whole lot of subcategories within the umbrella of virtualization: Hardware virtualization, Server virtualization, Desktop virtualization, OS virtualization, Network virtualization, Storage virtualization, Data virtualization, Application virtualization, Datacenter virtualization, CPU virtualization, GPU virtualization, and Cloud virtualization, to name a few.
There are different variations of hypervisors that enable one or more of the types of virtualizations listed above. They can run on specific, proprietary hardware, or independently of the hardware, depending on the environment or architecture. Storage hypervisors, for instance, act as a management interface for storage devices or networks, just as if they were servers. They can run inside an OS hypervisor, or even as a separate VM on its own.
Hypervisor Security
VM-based systems are technically isolated from the hardware, host OS, and each other, so any compromised VM shouldn’t typically affect the entire system. However, if the hypervisor itself is compromised, then data and applications in all VMs are threatened. Naturally, it is a prime target for attackers, because they gain control of all VMs and hardware by hacking into it.
Hypervisors are vulnerable to malicious code coming from rogue VMs. Such incidents have been reported but rarely publicized. In theory, it is possible to create rootkits (such as this and this) that install themselves as a hypervisor below the OS. This process is called “hyperjacking” and is difficult to detect or prevent, because this malware can intercept low-level machine code operations below the OS kernel.
It is best for IT security to know the workings of the hypervisor inside out, or at least use a known vendor who provides generic protection.
How to Choose the Right Hypervisor?
Choosing a hypervisor for a particular function depends on the size of the company, the criticality of the operations or workload, the capital and operational costs, the existing IT infrastructure, and the IT expertise and skills available in-house.
Typically, SMBs or organizations that are starting out with virtualization and hybrid clouds can make do with a Type 2 hypervisor that’s easier to set up. If latency is not a critical issue and the number of dynamic virtual machines needed isn’t very high, a Type 2 hypervisor is a great option.
On the other hand, when performance is an absolute must for the workload, and big data or business-critical transactions are processed, a Type 1 hypervisor is best suited. Enterprise admins can configure the hypervisors to dynamically allocate resources according to application priorities or peak usage times, as well as securely isolate VMs performing different functions from each other.
Some other considerations for choosing the appropriate hypervisor are:
Complexity: Is the hypervisor easy to deploy, manage, and troubleshoot? What does the console look like? Is it just software or a combination of hardware and software? Does it require a specialist to operate or will an IT generalist be able to get the hang of it?
For IT organizations that like to be in control of their virtualization and converged deployments, there are virtualization management tools available that show comprehensive views of multiple hypervisors and virtualization assets. Admins can monitor their connections to applications, servers, and storage devices, and act on the capacity planning and optimization recommendations. They can also identify and troubleshoot performance or security issues without logging in to separate hypervisor terminals.
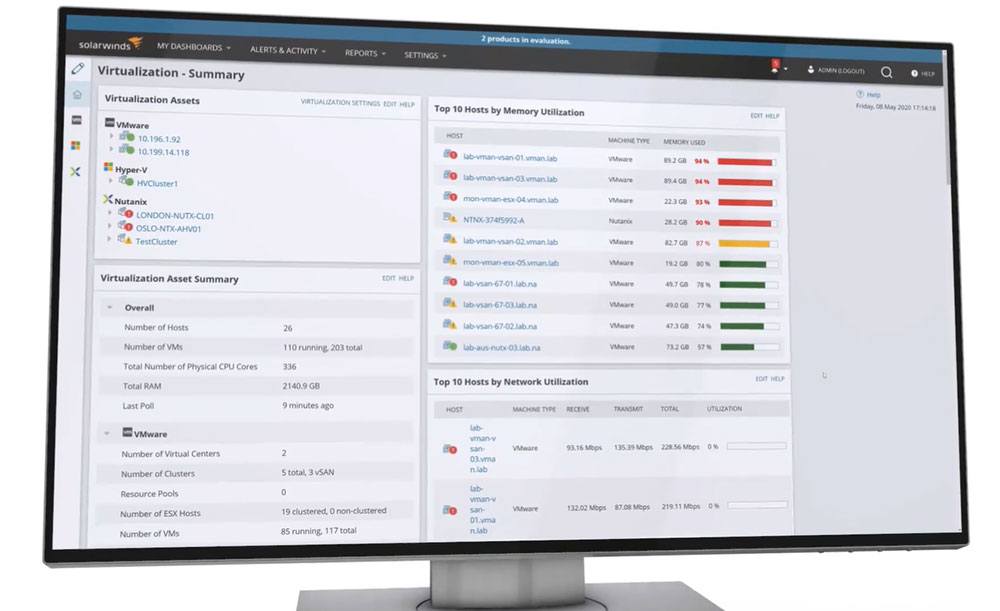
Source: SolarWinds Virtualization Manager
Cost: Is the hypervisor built into a larger solution or come as part of an infrastructure upgrade? What are the licensing fees, if any?
Enterprises that go for high levels of virtualization don’t necessary have the budget for licensing, especially when they’re non-profit or government organizations. Nutanix AHV offers a license-free, enterprise-grade virtualization stack as part of their private cloud or hyperconverged infrastructure (HCI) solutions, which supports a rich variety of OSes, cloud applications, and databases.
“AHV was a major selling point. We considered alternative virtualization platforms, but as well as the licensing costs – always an issue for publicly funded organizations like us – we wanted a virtualization platform that could take full advantage of other core infrastructure services, as well as one that didn’t require yet another management interface or the skillset to go with it. Nutanix AHV has given us all that,” explained Amardeep Rai, Head of ICT Programs for the Science Museum Group, UK. They saw 90% savings in licensing costs by virtualizing and migrating about 140 workloads to their new on-premises infrastructure.
Ecosystem: Does the hypervisor need to support a variety of hardware and all the widely used guest OSes? How does it communicate with or replace any legacy infrastructure that the organization is stuck with? Does it support all major technologies and apps such as Microsoft SQL Server, SAP, Hadoop, Splunk, and so on?
Containers: Container technology has emerged as a possible alternative to VMs in some scenarios. Containers allow an application to run independently of an OS, by packing it up along with related services, software libraries, and environment variables. A set of similar applications can then run on a “container engine” installed on any OS, vastly improving their portability. However, there are quite a few tradeoffs in using containers instead of hypervisors – number one being security – and so, neither is a replacement for the other.
With so many options and permutations available, it’s imperative that IT teams test and deploy a pivot hypervisor before making a final choice.
Hyperconvergence Is the New Virtualization
While hypervisors make the endless benefits of virtualization possible, time and technology wait for no one. Hyperconvergence – the poster child of hypervisors and convergence – has improved greatly upon virtualization by allowing compute, storage, and networking components of the infrastructure to remain discrete and scale independently, but providing at the same time providing a unified management interface.
It goes without saying that cost optimization and operational efficiency should be at the center of the decision to deploy or use any technology, including hypervisors.
Featured image: Pexels
Dipti Parmar is a marketing consultant and contributing writer to Nutanix. She writes columns on major tech and business publications such as IDG’s CIO.com, Adobe’s CMO.com, Entrepreneur Mag, and Inc. Follow her on Twitter @dipTparmar and connect with her on LinkedIn.
© 2020 Nutanix, Inc. All rights reserved. For additional legal information, please go here.



