COVID-19 brought unprecedented challenges to organizations cutting across size and vertical. But while everything from the economy to operations took a nosedive, one area of technology emerged strong, resilient, and in many cases, a savior. Cloud adoption rose steadily through the pandemic and after owing to its inherent advantages in enabling remote work.
In recent years, IT pros and decision makers from around the world have chosen the hybrid cloud as the ideal IT operating model for their companies, per the Nutanix Enterprise Cloud Index report. In the report was based on a survey with over 3,400 global IT professions, 86% of which consider hybrid their ideal IT operating model.
Organizations are increasingly moving towards hybrid multicloud environments in the race to improve team productivity, rapidly scale their IT infrastructure, secure their data, reduce operational costs, and ultimately create business value.
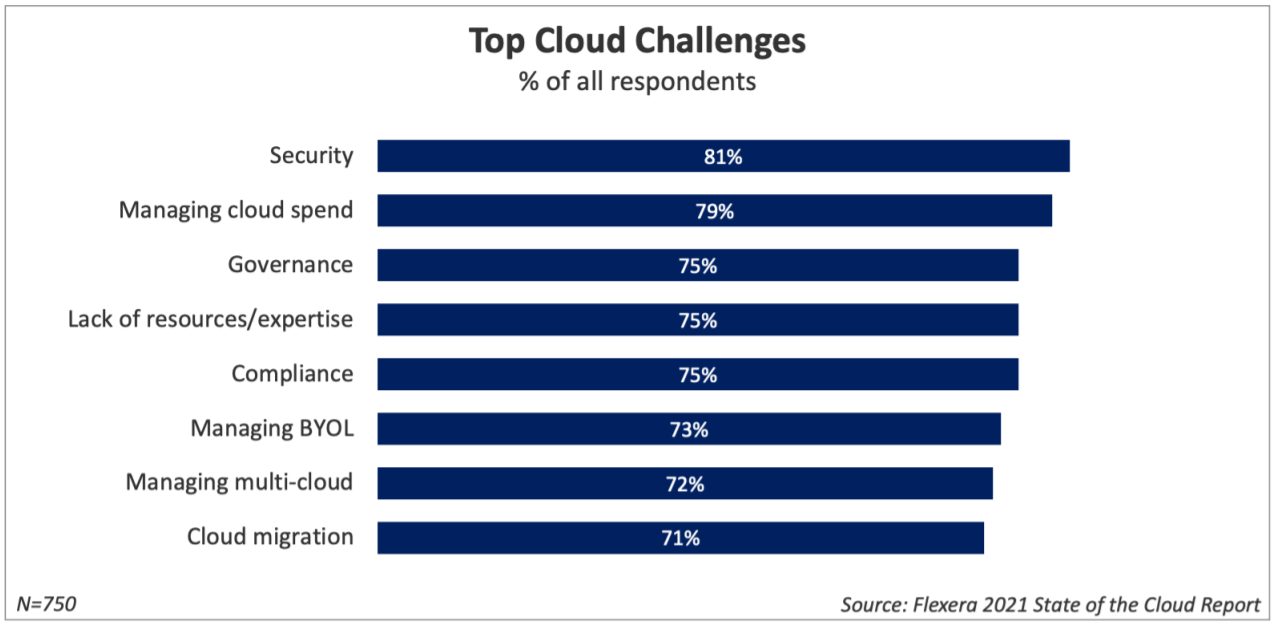
However, with all this scale, speed, and convenience comes complexity. And complexity breeds risks. Predictably, the Flexera State of the Cloud 2021 report found that security, spend, and governance were the top challenges in cloud computing for organizations of all sizes.
Here’s a look at the biggest risks in cloud computing and some ideas on how to manage them while cloud technology continues to evolve at breakneck pace.
Security Breaches and Unauthorized Data Access
Unauthorized data access is easily the biggest risk of cloud computing – or any IT infrastructure technology, for that matter.
Why? Nearly 100% of organizations that responded to an IDC survey said they had experienced at least one cloud data breach in the past 18 months.
Nearly two-thirds of them had sensitive data exposed.
Threat actors make money by selling or exploiting employee and customer data, and businesses are data goldmines. What’s more, cloud attacks typically evolve at a much faster rate than security defenses – cyberattacks are becoming more and more sophisticated, and IT teams are faced with the almost impossible challenge of keeping up.
Cloud service providers host data from hundreds of thousands of individuals at hundreds of businesses. In many cases, the entire cloud is vulnerable to a single point of failure. A successful attack could prove fatal for scores of companies and their customers across the globe.
A caveat: It’s not just outsiders seeking to gain unauthorized access to business data. Insider threats loom over cloud-based solutions just as darkly. Malicious, unsuspecting, or careless employees can bypass organizational access controls and download or upload files to an unsanctioned third-party cloud service.
Company networks could further be weakened by vendors to whom IT or other functional services are outsourced. In such cases, trust is shifted to their staff as well as other vendors they subcontract out to.
Mitigation strategy: Minimizing the risk of unauthorized data access in the cloud needs wholesome, integrated, and intensive security planning. Start with zero-trust security framework that requires all users to be continuously authenticated and authorized for every action they take.
“Organizations are coming to realize they should not automatically trust anything inside or outside their perimeter. That perimeter is more or less erased. So, now, we are seeing companies verifying everything trying to connect to their IT systems,” said Amit Bareket, CEO of Perimeter 81.
“With zero-trust security, policy enforcement and protection are easily implemented by isolating applications and segmenting network access based on user permissions, authentication, and verification. By implementing the ZTNA model for secure network access, IT teams can have full control over who is granted access, enters, and leaves the network at all times. This model has gained much more recognition since being mandated in President Biden’s executive order,” Bareket explained.
Other steps:
- Don’t forget the basics and IT security best practices. Use strong passwords and enable multi-factor authentication. Encrypt data at all levels – including at rest – to ensure it remains secure even if stolen.
- Understand the security risks in the public cloud. Only work with providers who have a proven track record of security.
- Put in place a cloud management strategy that defines performance and security benchmarks for all cloud technologies. Evaluate all applications from a security perspective before deployment.
Complexity and Costs
Cloud technology is rapidly advancing. In the aftermath of the pandemic, more businesses of all sizes are undertaking digital transformation efforts and moving more workloads to the cloud remains fundamental in this shift.
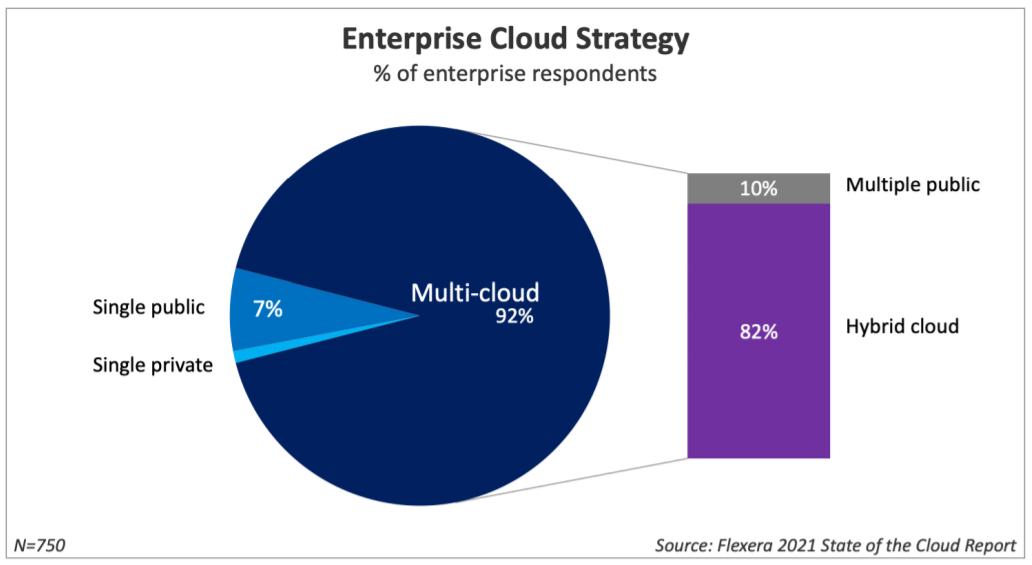
Organizations are struggling to keep up the pace of their operations and scale up to increasing customer demands. The Flexera report referred to earlier also found that 92% of enterprises today have a multi-cloud architecture in place, with four-fifths of those being hybrid cloud environments.
A study by GigaOm found that multi-cloud systems will be the norm across small and large organizations by 2025. For now, many enterprises have their workloads spread out over cloud as well as on-premises data centers.
So what’s the risk here? Complexity of deploying, maintaining, and upgrading the IT infrastructure.
The risk? Over-complication. When complexity increases, there is a growing need for skilled staff, more training for specialists, as well as budget for maintenance.
Mitigation strategy: As with anything else in an organization, adoption and championing of cloud computing needs to come from the top.
“The success of cloud adoption and migrations comes down to your people. Until you focus on the #1 bottleneck to the flow of cloud adoption, improvements made anywhere else are an illusion,” said Drew Firment, SVP at A Cloud Guru.
- Automate as many cloud maintenance tasks as possible. There are a wide variety of tools that automate cloud operations such as tracking and monitoring, application testing, and critical tasks like backup and recovery. Use them for governance, security, and cost optimization.
- Choose wisely between a public, private, or hybrid cloud architecture. Public clouds frequently offer leaner and smaller service packages while allowing for on-demand, pay-as-you-go upgrades. Hybrid clouds, on the other hand, let organizations choose between a CAPEX or OPEX operations and billing model.
Non-Compliance with Regulations and Laws
Many industries (especially health, finance, legal, and telecom) – as well as the government – regulate the working of organizations in their space. These regulations cover data, transactions, and IT operations, among other business functions.
For example, HIPAA requires all healthcare providers to protect patient data confidentiality. Similarly, PCI-DSS mandates that all business which accept credit cards need to safeguard customer data.
Companies operating in these industries need to establish controls and checks on the data storage, transfer, and access methods that they use. They also need to maintain stringent thresholds of uptime while provisioning for backups and data recovery. In several cases, outsourcing these functions to a third party or service provider may not be allowed, especially if that provider is headquartered in a different country.
As a result, many companies are unable to use public clouds for business-critical workloads or data storage. Those that are might need to make sure the vendors they’re relying on maintain a minimum level of compliance. They need to have policies and procedures in place for incident response, and even then, if a breach occurs at the cloud service provider, the company might still be liable to be prosecuted for it.
Mitigation strategy:
- Know the regulations and make sure all organizational tools, resources, and processes fully comply with them. Do due diligence; keep doing it.
- Train all IT staff – in fact, train all staff to understand exactly how laws and regulations affect their work in different roles. Re-skill them as frequently as needed.
- Ensure all vendors and service providers meet applicable standards and possess valid certificates and documents to show for it.
Insufficient Monitoring and Lack of Control
One of the goals of any cloud technology deployment (like any other) is better control over performance, quality, and outcomes. When the organization fails to establish control over these operational facets, it has a direct, detrimental effect on business continuity.
Further, an organization relies on a cloud vendor to maintain QoS at all times for its public cloud (or public cloud components of its hybrid cloud environment). When things go wrong, recovery depends on the promptness of the provider’s actions.
Mitigation strategy:
Implement a cloud management platform that abstracts the underlying architecture of different cloud systems and gives a ‘single pane of glass’ control to admins.
While selecting a cloud vendor, ask what guarantees they can offer in terms of compute, storage, and network performance and what their line of action is when disaster strikes. Put these down in the Service Level Agreement (SLA). Understand that risk is always shared in the public cloud.
Consider building and/or managing a private cloud when security, ownership, and performance take precedence over immediate capital expenditure.
Onward and Upward
The cloud has emerged as one of the biggest drivers of digital transformation because of the adaptability, accessibility, scalability, resilience, and flexibility it offers to businesses. It has enabled the development and adoption of new, disruptive technologies that have effected profound changes in the processes, competencies, and very business models of companies.
Such transformations don’t come without their share of risks. However, these risks can be mitigated to a great extent with a little forethought and planning.
“If you’re not willing to risk the unusual, you’ll have to settle for the ordinary,” Rohn said.
Editors note: This is an updated version of the original article published July 13, 2020.
Michael Brenner is a keynote speaker, author and CEO of Marketing Insider Group. Michael has written hundreds of articles on sites such as Forbes, Entrepreneur Magazine, and The Guardian and he speaks at dozens of leadership conferences each year covering topics such as marketing, leadership, technology and business strategy. Follow him @BrennerMichael.
© 2020 Nutanix, Inc. All rights reserved. For additional legal information, please go here.