In recent years, laptops and mobile phones have become affordable enough to be owned by individual users while having the capability to run application processes critical to workplace operations.
That – and the ubiquity of internet access – doesn’t in any way reduce the importance or need for the Virtual Desktop Infrastructure (VDI) environments that use large pools of VMs designed and configured for specific workloads. These can be transparently hosted on the cloud or on-premises data centers, providing on-demand, anytime, anywhere desktop interfaces for end users, making VDI one of the major applications of virtualization in the enterprise.
Disaster recovery: If a vulnerability is discovered in the image, the admin can simply rescind it and allocate a different version. In the event that some sort of malware or virus has penetrated a specific node or the underlying host of a VM is compromised, the admin can delete the guest OS or clone image on that node and move the VM to a different, healthy host, with little chance of it affecting the host OS or master image.
Timely patch management: Unpatched endpoints with applications or OSes that haven’t been updated to the latest versions are huge risks in massive networks. In the old days IT had to manually “push” updates to individual systems, adding delays to the process. VDIs enable admins to use a secure “golden image” that they can centrally update as and when required, bearing in mind the hardware and network requirements of the appropriate segment of end users.
Data privacy and regulatory compliance: Control over data access and storage is critical for organizations in finance and healthcare. VDI enables better data governance with centralized access policies, handling and masking of personally identifiable information (PII) and financial or medical data, and secure updates of data.
In spite of – and in some cases, because of – these compelling security advantages, VDI (and its cloud equivalent DaaS) is often marketed as a be-all, end-all solution that scales. However, VDI security is not a given, nor is it completely immune to hacking.
The Need for a Foolproof VDI Security Plan
The consistent advancements in virtualization technology have led to widespread adoption of VDI, within both temporary and permanent operational scenarios. There are a number of benefits (which also double up as risks) that VDI brings to various business functions, the biggest being cost savings and reduced TCO.
VDI is ideal for organizations that have a large number of users who need only a limited set of applications (think call center or Android game developers). Add to that the massive shift to work-from-home in the aftermath of the COVID-19 pandemic, and it’s easy to replicate inexpensive copies of virtual OSes on hundreds of thousands of devices.
A survey by Gartner revealed that nearly three quarters of the 300+ CFOs they surveyed are looking at remote work as a cost-cutting measure. “CFOs, already under pressure to tightly manage costs, clearly sense an opportunity to realize the cost benefits of a remote workforce. In fact, nearly a quarter of respondents said they will move at least 20% of their on-site employees to permanent remote positions,” said Alexander Bant, VP of Research for Gartner’s Finance practice.
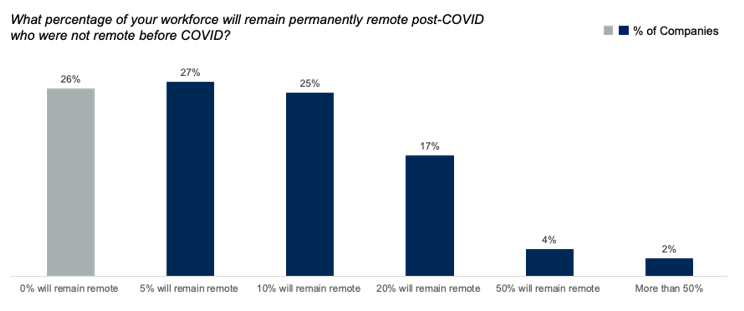
In many cases, this pressure or overzealousness in cost-cutting – as opposed to cost “optimization” in IT – might leave open a security vulnerability that can be exploited by attackers.
Further, there are some practical realities that all IT teams managing VDI deployments have to contend with.
For one, companies are facing a huge challenge adjusting to the large and sudden shift of employees working from home or remotely in the wake of COVID-19. The “virtualized endpoints” or nodes that they use to connect to corporate servers can potentially become ground zero for all sorts of logging, intrusion, social engineering and man-in-the-middle attacks.
In pre-VDI times (or even in pre-COVID times) user devices with sensitive corporate data were either located on-premises or owned by the company; thus, data and applications were hardened and configured to operate within the perimeters of organizational security. When VDI and cloud became more pervasive, this created an illusion of isolation.
Pretty much every organization enables their users, vendors and partners to connect their own devices to the enterprise network. Employees’ laptops and smartphones frequently access privileged IT assets, including sensitive data and apps, customer records, financial information, proprietary source code – via critical infrastructure pathways and networks. And these laptops and smartphones rarely comply with the company’s security policy or any meaningful security standards.
As a result, endpoint device security is probably the weakest link and the biggest priority in VDI security.
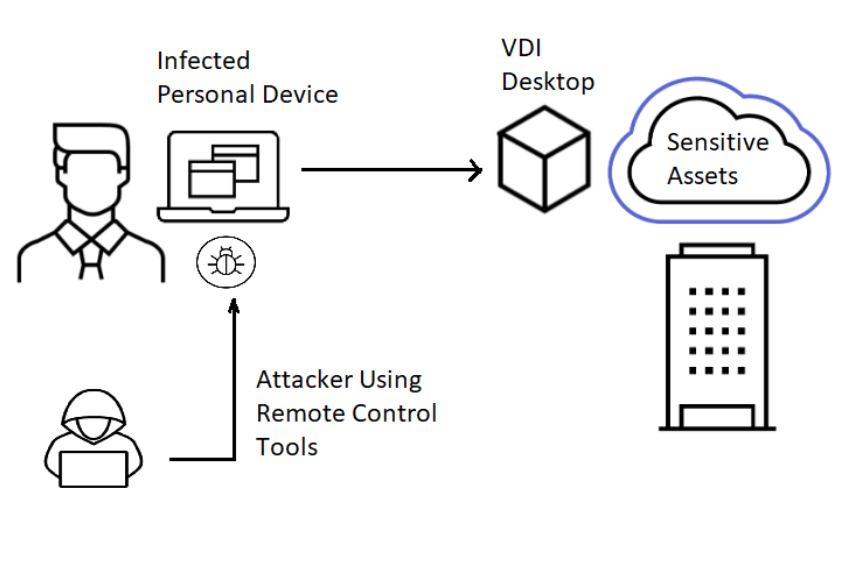
Once an attacker breaches or takes control of a node, they can potentially compromise the application underlying the workload on the VDI, or even get a foot in the door into the enterprise network and data center.
And with increasing amounts of unverified – and potentially compromised – traffic coming in to company servers from different locations, the on-premises or cloud security software – as well as its endpoint client have to scan huge volumes of memory and networks, and generate and report error logs. This, of course, requires considerably more bandwidth and compute power, saturating the endpoint device and in many cases, defeating the purpose of VDI itself.
Addressing Security Risks and Challenges in VDI Deployments
It isn’t simple to mitigate and manage threats while maintaining functionality and improving performance and user experience in a VDI. Keeping the perimeters secure and hardening the servers is paramount. While there is no magic bullet, there are certainly a few simple security measures IT can take to keep the VDI going.
Preparing for the worst: It is inevitable that desktops and other endpoint devices in the VDI will be breached. With unsecured Wi-Fi networks, unhardened applications (think Zoom) and plain-text email vulnerable to scanners all over the place, attackers have a target that is far easier to get into than a protected corporate desktop, and one that is probably already compromised or has gaping security holes.
Even if a desktop breach is detected, it could be a time consuming process to determine how it happened and the extent of damage that has been done. Recovery and restoration of functionality depends on the scale and complexity of the infrastructure.
Choosing a reliable login method: There are two options for users to log in to the VDI. One is Single Sign-On (SSO), or one login for accessing all resources. While this may seem risky on the face of it (once a hacker has the password, they can access all the user’s privileges), the advantage is that the user has only one password to remember, and therefore, will likely not write it down anywhere. SSO is ideal when users have to access services or apps that live outside their desktops, like SaaS.
The other is two factor authentication, which needs multiple credentials and actions for logging in – such as a password entered in the desktop and a tap on the mobile screen, or logging into a VPN and then into a service delivered by browser. Naturally, this is innately more secure than SSO. It’s up to IT to choose a method that suits their users, based on users’ levels, application requirements, sensitivity of the data, or capabilities of the system and network.
Managing user identities: This is based on the Zero Trust model, which stipulates that users need to be given access to only those resources that they need for their role or tasks assigned to them, and nothing more. Policies specify user and group roles, and monitor and control active sessions individually for all logged in users. This prevents an attacker from infiltrating a user session and accessing sensitive data or getting into the server laterally.
Application segmentation: Applications and workloads can be built in such a way that they are isolated and separated from other business-critical or sensitive applications in the VDI. Granular policies based on processes, resources, or other assets go a long way in cutting vulnerabilities down to size. Ring-fencing segments within the VDI ensures that attackers can’t achieve lateral movement in the event of a breach.
Combined with user identity management, IT can make sure all users can access only those services and parts of the application they need to, and don’t move out of their relevant environment.
Rigorous data protection policies: Modern hackers are more interested in stealing data and intellectual property than breaking into servers or networks and doing damage. VDIs allow for more stringent data control and IT should take advantage of this. To start with, data should never leave the data center or central server, whether on-premises or in the cloud. Data center resources can be used for automatic backup and recovery of desktop data. All data in transit should be encrypted.
Comprehensive visibility: The security solution or VDI management platform should allow admins to monitor in real time (on-demand) the following parameters:
- all the nodes that are online
- whether each desktop or VM is updated and patched or not
- every user that is logged in, along with activity logging
- the processes and services running on each server and node
- which applications and services are being used for what purposes, by which sessions
- all the flows that are being generated
- how processes are communicating
Continuous, automated endpoint security management: It is critical for IT teams to ensure that endpoint software and hardware remain compliant with the security policies and standards of the organization at all times. A secure VDI needs automated checks and approaches to software installation and removal, patches and upgrades, anomaly detection, and support procedures at the endpoints.
Proactive incident response: It’s a myth that virtual desktops are immune to attacks and security breaches. Granted, they have less vulnerabilities than physical desktops, but they are still susceptible to various types of keyloggers, screen scrapers, malicious email links, Remote Access Trojans (RATs), and lateral movement. Non-persistent desktops are even prone to antivirus boot storms (signature and algorithm updates that spike usage), leading VDI vendors to recommend turning the antivirus updates off.
The solution, therefore, is having a pragmatic incident response process that expedites threat mitigation and recovery, while minimizing disruption to operations. As soon as an infected VM is discovered, it needs to be blocked and isolated from the network, or even terminated if necessary, with a focus on salvaging user data.
VDI as a Game Changer in IT Security
The increasing adoption of hybrid, multicloud environments and hyperconvergence is changing virtualization in complex ways, leaving security professionals on the edge. However, virtualization itself has changed the way data centers work, forced the upgradation of legacy infrastructure, and is now pushing organizations towards more scalable and robust infrastructure deployments.
As more everyday transactions become technology-based, and work from home becomes more commonplace, companies will need security solutions that detect and prevent complex malware while consuming less resources and bandwidth. This turns traditional security practices on their head, because of the lack of centralized control or enforceable standards. Therefore, it wouldn’t be surprising if effective solutions in VDI security will set the direction for IT security as a whole.
Dipti Parmar is a marketing consultant and contributing writer to Nutanix. She writes columns on major tech and business publications such as IDG’s CIO.com, Adobe’s CMO.com, Entrepreneur Mag, and Inc. Follow her on Twitter @dipTparmar and connect with her on LinkedIn.
© 2020 Nutanix, Inc. All rights reserved. For additional legal information, please go here.



