The race towards the cloud is well and truly underway in the enterprise. In their quest to improve operational efficiency, save costs, and create business value with technology, companies are embracing a hybrid, multicloud environment.
Still, that doesn't mean that those who embrace hybrid cloud automatically have data security and compliance all sewn up. While hybrid cloud environments are inherently secure in themselves, companies moving every imaginable workload to disparate private and public cloud systems are using a patchwork of security policies and protocols that give rise to new complexities and pose serious security risks.
“The modern post-COVID company is a million-armed octopus in thousands of locations, and every arm is a digital access point that can be compromised by script kiddies, social hackers, professional criminal hacking organizations, or even nation-state actors,” said John Koetsler, CEO of SSMRT.
“Only by managing security in all those million access points can a company ensure safety … and avoid becoming another ransomware story on national news.”
Unsurprisingly, security and privacy are the top factors that influence any cloud infrastructure design, according to technology specialist Steve Prentice.
“Hybrid cloud deployments can quickly transform into a multiheaded monster that places an increasing burden on already overstretched internal security teams,” said Prentice.
IT professionals are particularly concerned about the security of workloads that run in the public cloud part of the hybrid setup. And though public cloud providers have instituted solid physical security measures and maintained documented, stringent standards for protecting their infrastructures from intrusions, high-profile attacks like the Capital One AWS data breach are a constant reminder that no one is immune.
So what can security professionals do to secure the perimeters of their hybrid cloud environment and still enable functionality, interoperability, and ease of use? Here are some small and large steps they can take.
1. Take a Holistic Approach to Data Security
When data is managed throughout its entire lifecycle, it increases the chances of timely identification of vulnerabilities, enforcement of policies, and threat detection and mitigation.
"When data is spread across cloud and on-premises repositories, organizations need to take a holistic approach to its security," said Ilia Sotnikov, Security Strategist & VP of User Experience at Netwrix.
It is in the interest of enterprises to centralize management of the whole IT infrastructure and deploy a unified monitoring solution that gives end-to-end visibility and control.
Also needed is an identity and access management solution that provides tight control over data access, if not a zero trust framework.
Hybrid cloud provides additional layers of security between private and public clouds.

Source: Nutanix
"The cloud can be as secure, or insecure, as any traditional IT infrastructure," warned Doug Howard, CEO of Pondurance.
In the same vein, organizations shouldn’t forget to plan security for future expansions. A comprehensive cloud management strategy can act as the guidepost to scaling and upgrading infrastructure needs.
2. Standardize Processes
Security policies need standardization as much as any business process. Some of the biggest data breaches happened because data access controls weren’t applied equally well on all parts of the IT infrastructure. The same set of security procedures for various actions – such as logging into apps, creating VMs, etc. – that apply on-premises should be replicated on public cloud components.
Yangzhi Zhao, product director of Nutanix Frame, offered a three-step approach for getting started:
- Conduct a comprehensive assessment of the current security posture and risk exposure. Identify and prioritize sensitive applications and data that need to be protected.
- For all sensitive applications and data, granularly define which users and integrated applications/services require access to a particular asset, and in what contexts.
- Implement security solutions to restrict access to the identified sensitive applications and data in a “least-privileged” approach, along with multi-factor authentication.
Enterprises need to be extra watchful to prevent shadow IT practices cropping up here and there. Too often, developers tend to bypass security procedures in their over-eagerness to get work done.
A note on data encryption: All data, whether in transit or at rest, must be encrypted. It should encompass client-side, server-side, and network traffic. Many cloud vendors and managed service providers have made data and file system encryption an integral part of their security services. Cloud admins need to maintain the same level of encryption across multiple clouds and between private and public clouds.
3. Pay Extra Attention to Public Cloud Components
Every hybrid cloud system is a delicate balance of public and private cloud components. Workloads move from private or on-premises to public cloud for a variety of reasons, one of the biggest being simplicity. However, security concerns in the public cloud must be addressed before any such migration.
Hybrid cloud environments are often a mishmash of legacy applications hosted in a data center and newer ones (including cloud-native apps) hosted on public clouds. This makes the hybrid cloud vulnerable at places where the original technology is extended or modified.
“Think of it like your garage,” said Mike Lloyd, CTO of Redseal Networks. “If you’re running out of space, you could rent space from your neighbor’s garage, and this adds some flexibility. The trick with this kind of approach is to make sure ‘your’ part of your neighbor’s garage can only be opened by you. If you’re not careful, you may find that your stuff disappears.”
Cloud adopters assume that security is the responsibility of the cloud provider, which can leave organizations vulnerable to internal attack vectors and human error. Though large cloud vendors relieve as much operational burden from their customers as possible and also give certain basic guarantees, ultimately the customer is responsible for data, apps, configuration, and updates.
“Security and compliance in the cloud is a shared responsibility between the cloud service providers (CSP) and their customers,” said Diem Shin, Product Lead at Telos Corporation.
“Under the Shared Responsibility Model, the CSP is responsible for security ‘of the cloud’ which includes the hardware, software, networking, and facilities that run the cloud services. Organizations (the CSP’s customers), on the other hand, are responsible for security ‘in the cloud’ which includes how they configure and use the resources provided by the CSP.”
4. Beware of Human Error
Human error is arguably the weakest link in cloud security. Gartner estimates that up to 95% cloud breaches are caused by human errors, a WSJ article reported.
“One of the biggest factors at play is still human error,” said Shayne Sherman, CEO of TechLoris. “The best way to stay on top of this is to first make sure that employees go through regular security training. Making sure that everyone is up-to-date on the latest phishing tactics can be a life saver.”
Organizations need to staff right and employ in-house experts to manage the assorted configuration settings needed to keep a hybrid cloud environment running.
Over 90% of security pros responding to a Tripwire survey expressed fears that human error would cause accidental exposure of data residing in their company’s cloud systems.
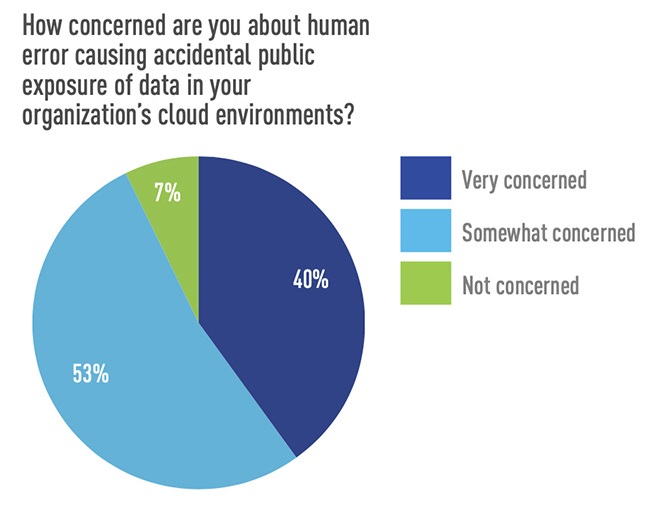
Source: Help Net Security
In a post-pandemic world, organizations need precisely defined security procedures for remote work via End User Computing (EUC) and associated shifts such as Bring Your Own Device (BYOD) and Choose Your Own Device (CYOD). It’s also necessary to develop and implement security policies for onboarding and exiting permanent employees or temp workers, especially as the organization scales.
For example, make sure departinig employees no longer have access to internal systems after they exit.
5. Fill Skill Gaps with Managed Services
A McKinsey study found that CIOs across enterprises are prioritizing infrastructure modernization in order to increase agility, provide better QoS to customers, optimize costs, and reduce security risks. They also see hybrid cloud as a predominant enabler of IT architecture modernization.
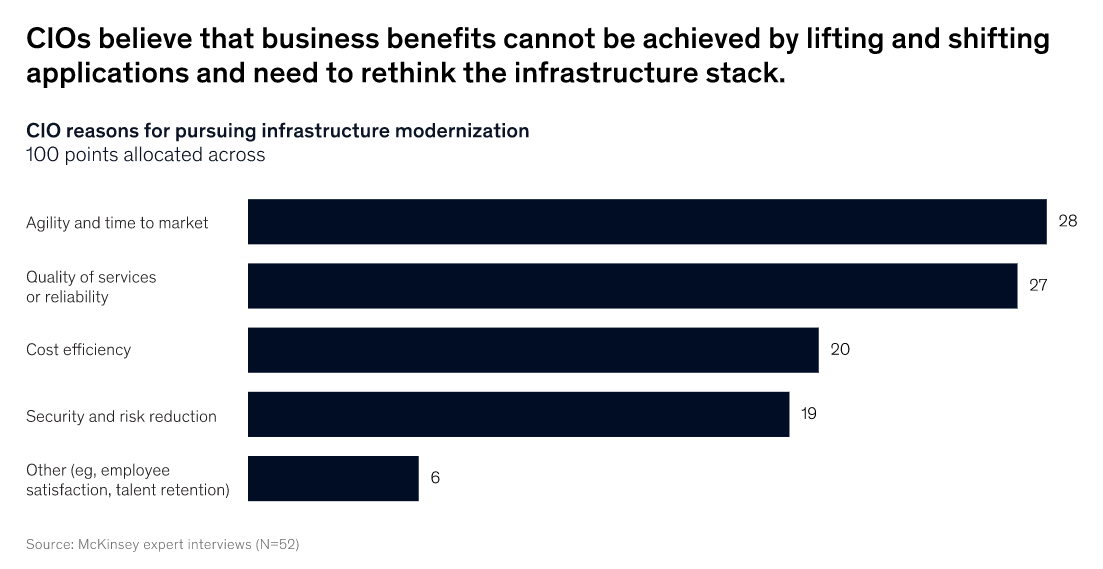
Source: McKinsey
Emerging hybrid cloud technologies frequently prove too complicated for IT departments used to running legacy infrastructure. Organizations can consider hiring an Managed Service Provider (MSP) to maintain the hybrid cloud infrastructure and manage security across platforms.
“Managed hybrid cloud can help reduce or eliminate redundant information stored in individual silos and provide organizations with better control over their security profile through encryption, automation, access control, orchestration, and endpoint security, to name a few,” explained Gene De Libero, CSO at Geek Hive.
Bell too stressed the importance of working with a trusted advisor or technology partner to help plan effective internal security strategies over time.
MSPs bring to the table a breadth of skills, best practices, and lessons learned from a multitude of customers. This greatly elevates the level of security available to the organization.
“Letting the experts do the work for you is the best way to succeed in this new world; managed services offer many options to help migrate, modernize, transform and mitigate risks,” concurred Kim Stevenson, Board Member at Skyworks Solutions and Mitek Systems.
6. Collaborate Closely with Vendors
Cloud vendors are constantly building IaaS, PaaS, and SaaS systems with different levels of complexity and requiring skills in myriad programming languages, scripts, database systems, and so on. Even data portability among these platforms becomes a pain, let alone integration.
Enterprise customers ideally shouldn’t choose a cloud vendor without putting in place legally reviewed SLAs that clarify every detail about data control and access, storage, transfer, redundancy, replication, and recovery. Further, these might work for current resource needs and budgets, but no longer apply if the infrastructure scales. The organization may also need to spend more for data and app migration capabilities in order to avoid vendor lock-in.
“Treat cloud vendors like you would any partner,” said Suni Munshani, CEO of PatternEx.
“If you would not trust your partners to possess your sensitive data in the clear, do not give it to them. If you would not trust them to hold an encryption key, do not give it to them. Address these major questions before moving critical data to the cloud.”
Balancing Mobility, Innovation, and Control
COVID-19 has brought to the fore unprecedented changes in workplace practices. Users with myriad device types, each configured in a different way, with zillions of apps to boot, are demanding anytime, anywhere access to the company network.
It follows that the hybrid cloud security puzzle could get more complicated.
“Control and innovation are not friends,” declared Lloyd. “Each one tends to break the other unless applied with care and a light touch.”
Piecing hybrid cloud security together isn’t easy, but rapid innovation is underway to make different system interoperable, seamlessly.
“Ultimately, cloud structures will be so complex that people cannot understand them anymore. When that time comes, machine reasoning will be in order,” Lloyd predicted. “It’s the only viable response. Computers will uncover all the mistakes we make as we pile up all this technology, one small step at a time.”
Until then, the best practices for hybrid cloud security continue to be driven more by people and processes than technology.
Editor’s note: This article originally appeared on February 20, 2020. Learn what global IT leaders about hybrid multicloud operations in the 2022 Entperise Cloud Index.
Dipti Parmar updated this article in May 2022. She is a marketing consultant and contributing writer to Nutanix. She writes columns on major tech and business publications such as IDG’s CIO.com, Adobe’s CMO.com, Entrepreneur Mag, and Inc. Follow her on Twitter @dipTparmar and connect with her on LinkedIn.
Charlotte Jensen is a contributing writer who specializes in business topics. She is the former executive editor of award-winning Entrepreneur magazine. Find her on Twitter @JensenChar.




