One of the most consistent things about IT technology is change - high rates of change. New technologies in hardware, software, and deployment models are always being implemented. As IT is at the forefront of how modern businesses operate and even differentiate themselves, it should be no surprise that those that seek to disrupt, steal, or profit from malicious activity are also improving and changing their technology and approach. Modern applications are distributed across multiple platforms and locations - blurring the lines of the datacenter. This concept may be great for performance and availability but it can make data and application security a bit more complex. Despite the constant change in the IT and Security technology landscape, one thing that has remained constant is the growing sophistication of modern attacks such as zero-day, advanced persistent threats, and ransomware, to name a few.
Policy is the New Security Perimeter
There was a time when the security concept of “defense-in-depth” was simple to conceptualize, as it was based on easy to understand constructs like physical locations or internal vs. external networks, and creating layered perimeters by adding detection and controls at logical ingress and egress points. With the distributed nature of modern applications and the inclusion of public cloud and hybrid cloud architectures, those perimeters are no longer simple to define. For this reason, the older models of security perimeters must evolve. Defining a perimeter based on the security concept of “Zero Trust” shifts the focus to the application, and causes the user to make policy around the new perimeter. Zero trust removes “us vs. them” and “inside vs. outside.” It presumes that an attack can come from anywhere, and thus the best defense is to limit network communication and authorization to what’s required for an application to function, rather than relying on trusting the location or source.
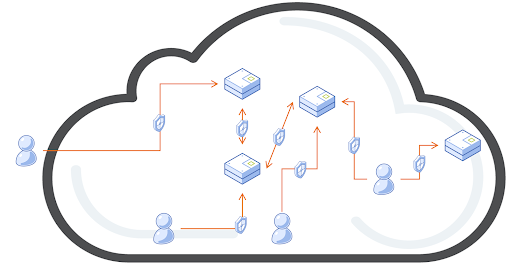
2020 and the pandemic also brought us the rise of work from home (WFH) and rapid expansion of virtual desktop deployments, which adds one more difficulty in defining the perimeter - remote workers. This brings us to the main focus of this blog, which is not only to set the stage for how Nutanix is looking at security in hybrid cloud environments, but to also catch you up on what we have been doing around network security.
As you may know, Flow is our network security product for AHV virtualization environments. It uses microsementation to protect applications and virtual networks running on Nutanix. In the past few releases we have added specific enhancements to address WFH concerns of remote workers and make the overall process of managing policy in Flow simpler.
Role of Identity in End User Computing
Identity has always been the focal point of End User Computing (Virtual Desktops or DaaS), where a desktop or an application is often linked to a specific user or group. In AOS 5.17, we added a feature called Identity Firewall (IDFW). IDFW allows for Flow policy to incorporate the additional context of user identity. Consider the ability to author Flow policy to limit a virtual desktop to a set of endpoints based on the identity of the user. For example, using a single pool of desktops on a flat network, it’s possible to create a policy that does more than block desktop to desktop communications. This can also provide a unique network policy that limits contractors to specific applications and can control employee access to networks or applications based on their roles as defined in directory services. The benefit of policy defined in this way is that, as roles or employment changes, it allows the network policy to automatically adapt. There’s no need to manually reprovision or alter user configuration in the desktop solution.
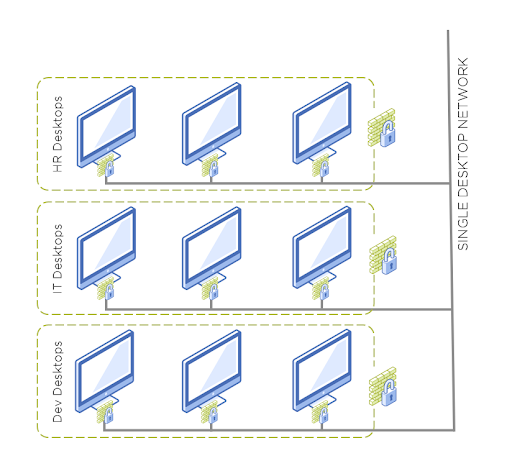
Ensure Consistent Policies with Reusable Groups
The policy model in Flow is based on the concept of using tags or categories to group endpoints (e.g., Web servers, databases, middle tier application services, etc.) in an effort to reduce the complexity and need for policy updates in dynamic virtual environments. In a virtual environment where the hypervisor has the context of endpoint identifiers (IP address), and those identifiers can change dynamically (DHCP, network move, adding a network interface), it makes far more sense to write policy in terms of grouped VMs, rather than enumerating IPs and then needing to update policies when those values change. In addition to the use of categories, Flow policy allows the use of Service Groups to represent a set of ports and protocols under a single alias and Address Groups to group non-virtual endpoints or reference address ranges. This greatly simplifies writing policy for non-virtual external endpoints such as clients, corporate networks, and bare metal.
Plan, Monitor, and Audit with Flow Security Central
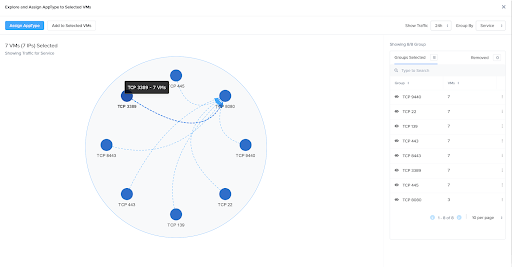
In addition to the simplification of policy via groups and categories, we recently expanded the Flow functionality with the addition of Security Central. Security Central, an included feature of Flow, is a security operations and analytics dashboard and was launched in October at our .NEXT conference with a key feature that provides VM traffic visibility. Security Central takes network flow data and builds an interactive visualization of VM to VM traffic. This visualization provides a much easier way to gain context of network traffic and make decisions on categorization or grouping of VMs. In the current version, the focus is on simplification of category creation; future releases will look to provide policy suggestions as well. You can learn more about the other features and functions found in Security Central in our launch blog post.
Security and Hybrid Clouds
There’s lots of discussion around using hybrid cloud models to ensure enterprises can get the best of on-prem and public cloud operating models for their applications. A common concern for many organizations when considering hybrid cloud is how to ensure their security policy is consistent across all locations. For hybrid cloud, Nutanix offers Clusters, which allows deployment of our platform onto AWS instances today, and Microsoft Azure in the near future. The great thing about Clusters is that it’s the same Nutanix platform that runs in on-prem datacenters, and that includes the option to use Flow for network security. When all locations are managed via Prism Central, the benefit is that categories and security policy are also available at all locations. This eliminates the need to manage network security differently or separately for on-prem or cloud, as it's all consolidated in Prism Central for policy and Security Central for visibility and security operations.
Enhancing Security with Partners
While we believe that Flow can cover a large number of network security use cases, there are use cases where it’s necessary to not only segment networks and applications but also to examine the traffic that is allowed in the network. Whether it is for regulatory purposes, or as part of a comprehensive strategy to defend against ransomware, the ability to add network-based threat intelligence is a valuable option. Nutanix Flow supports this policy-based service insertion of 3rd party virtual security appliances to provide granular control of when and where additional inspection is applied.
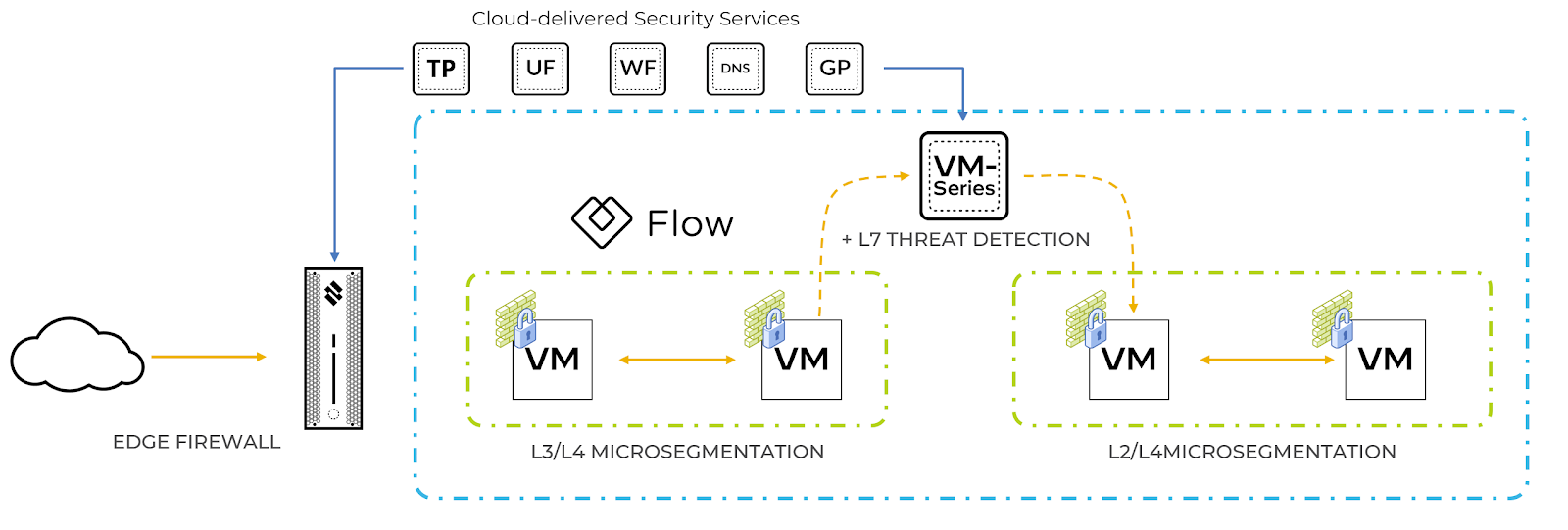
As an example, one of our service insertion partners, Palo Alto Networks, not only can be used for advanced threat intelligence, but also extends their integration into security management. Palo Alto’s management application, Panorama, by integrating with Nutanix Prism, incorporates the Nutanix policy categories into its dynamic access groups (DAGs). This integration helps ensure firewall policy and context are consistent across the platforms. In addition to Palo Alto Networks, Flow supports L7 integration with Fortinet FortiGate-VM and SonicWall NSv on AHV, and our integration with Gigamon GigaVUE virtual appliance allows VM to VM traffic monitoring in the Nutanix environment.
Ready To Try It Out? Take a Test Drive!
One last recent addition is the availability of our Flow Test Drive. Nutanix Test Drives give you the chance to interact with a real Nutanix deployment aided by a guided walkthrough of the product features. In our Flow Test drive you can see how easy it is to enable Flow and get an interactive walkthrough of categories, policy types, and an example of policies in action. Take a Test Drive Today!
© 2020 Nutanix, Inc. All rights reserved. Nutanix, the Nutanix logo and all Nutanix product, feature and service names mentioned herein are registered trademarks or trademarks of Nutanix, Inc. in the United States and other countries. All other brand names mentioned herein are for identification purposes only and may be the trademarks of their respective holder(s). This post may contain links to external websites that are not part of Nutanix.com. Nutanix does not control these sites and disclaims all responsibility for the content or accuracy of any external site. Our decision to link to an external site should not be considered an endorsement of any content on such a site. Certain information contained in this post may relate to or be based on studies, publications, surveys and other data obtained from third-party sources and our own internal estimates and research. While we believe these third-party studies, publications, surveys and other data are reliable as of the date of this post, they have not independently verified, and we make no representation as to the adequacy, fairness, accuracy, or completeness of any information obtained from third-party sources.
This post may contain express and implied forward-looking statements, which are not historical facts and are instead based on our current expectations, estimates and beliefs. The accuracy of such statements involves risks and uncertainties and depends upon future events, including those that may be beyond our control, and actual results may differ materially and adversely from those anticipated or implied by such statements. Any forward-looking statements included herein speak only as of the date hereof and, except as required by law, we assume no obligation to update or otherwise revise any of such forward-looking statements to reflect subsequent events or circumstances.